How it Works Discover how the API Security platform works in practice
Our Developer-First API Security Platform makes it easy for developers to build and automate security into their API development pipeline speeding up the delivery cycle as opposed to slowing it down. Security teams retain full visibility and control of the security policy enforcement.
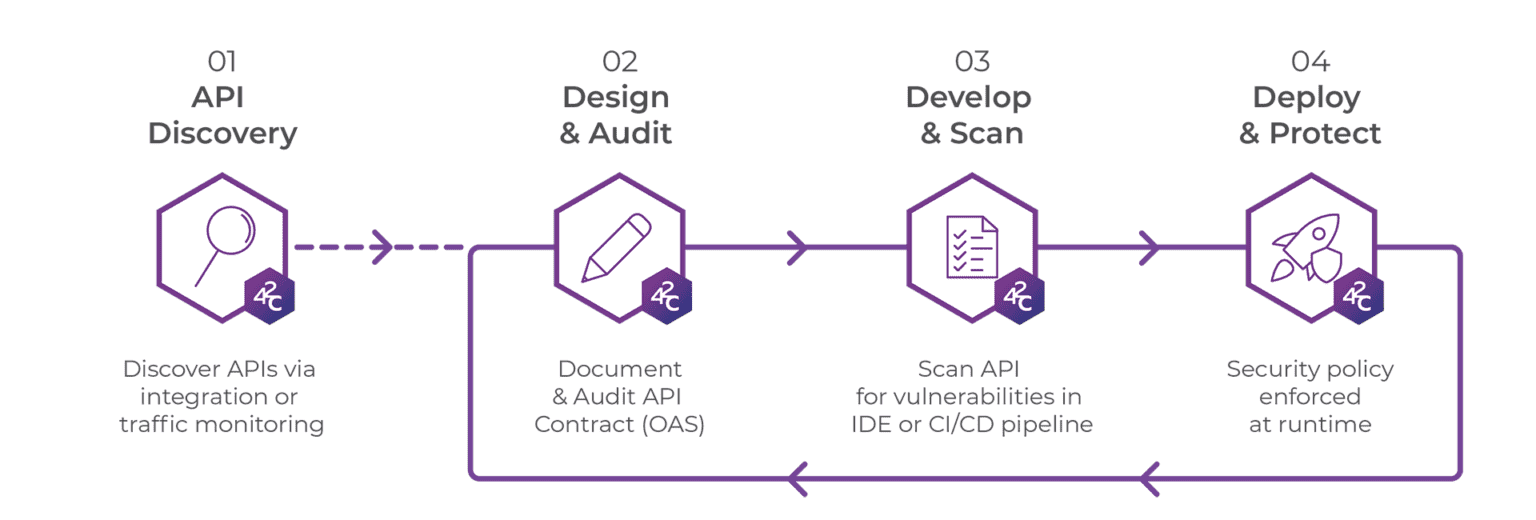

01 API Discovery
Quickly discover and create an inventory of all your APIs at both design and runtime via the platform’s Github repository integration. API discovery via network traffic monitoring can also be used at runtime to discover APIs.

02 Design & Audit
Define all the elements of your API in an OpenAPI contract. OpenAPI contract can be created or edited using our free OpenAPI(Swagger) Editor extension available for leading IDEs. There are multiple advantages to this design-first approach to API development. Security teams also have the capability to provide security policies that can be integrated into the OpenAPI contract at design stage.
The OpenAPI contract is audited using API Audit directly from the IDE extension. It conducts a static analysis of your API definitions and looks at the quality of the OpenAPI contract in terms of structure and security vulnerabilities. The tool scores and suggests fixes for any identified weaknesses.

03 Develop & Scan
Once the OpenAPI contract is of sufficient quality then the API can be written by the development team. It is possible to auto create the code directly from the OpenAPI contract using code generator tools such as OpenAPI Generator or Swagger Codegen.
Operations within the API are scanned by our API Scan tool within the IDE to ensure they conform to the approved OpenAPI contract. Developers quickly ensure individual operations match the design before they move onto the next operation.
Once complete the API can also be scanned by the API Scan tool in the CI/CD pipeline. The tool gives instant security scoring for prioritization and remediation advice. Scanning at this stage is particularly useful for both development and security teams as it ensures conformance of the API with the design and security policies, prior to deployment.

04 Deploy & Protect
The API Protect API micro-firewall enforces the API security policy at runtime. It uses the OpenAPI contract to create an “allow list” to constrain the API traffic both on request and responses. Security teams retain full control over the security policy and the firewall automatically updates each time the API changes. This positive security approach ensures low false positives and low false negatives. There is also minimal impact on latency (less 1 millisecond) allowing it to be deployed at scale across your entire enterprise.
Ready to Learn More?
Developer-first solution for delivering API security as code.
