CI/CD
Secure APIs from inside your CI/CD Pipeline
OWASP has identified “Improper Assets Management” as one of the 10 Most Critical API Security Risks.
Running the 42Crunch API Audit from inside your Continuous Integration and Continuous Development (CI/CD)
pipeline prevents unsecure APIs from reaching production.
Optimize your OpenAPI files
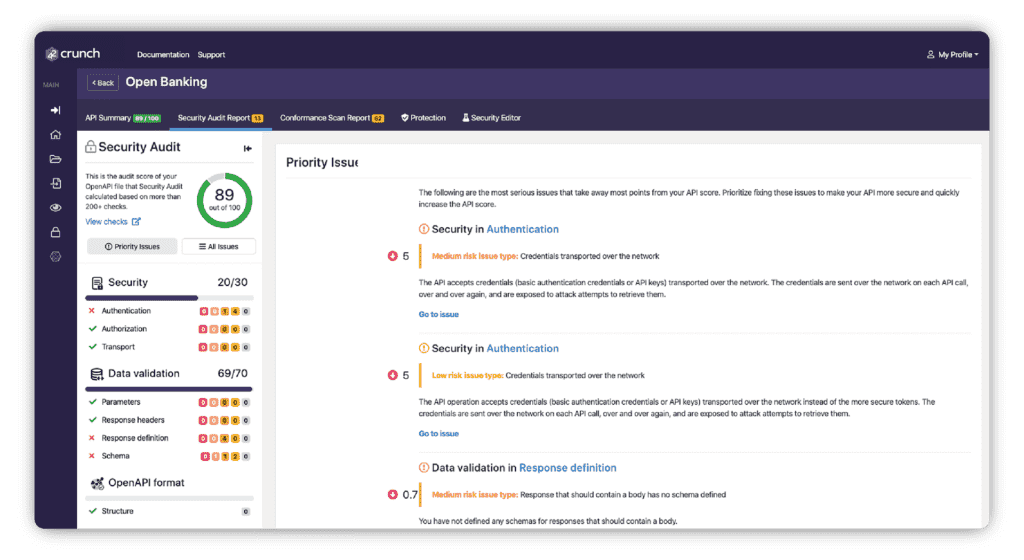
42Crunch API Audit powers your Continuous Integration and Continuous Development (CI/CD) pipeline by acting as a linter to conduct an analysis of your OpenAPI (Swagger) files.
It performs a static analysis of each of the OpenAPI definition files by running over 300 checks that enforce best practices and identify potential vulnerabilities.
An auto-generated report identifies any issues, ranked by severity, across a number of criteria such as security, data validation, schemas and specification format. It also offers remediation advice on how to fix these issues.
Single Source of Truth
The OpenAPI definition file makes it easy for DevSecOps teams to adhere to the highest quality standards as everyone is working on a single shared source of truth. Prior to pushing the API into production, developer and security teams test the API against the OpenAPI contract to ensure the actual API matches its definition. This positive security approach is superior to that of traditional Static Application Security Testing (SAST) tools, which are limited by lengthy scan times and poor accuracy, returning too many false positives, and eroding developer trust.
Check out our other integrations
Colin Domoney
Leverage the declarative nature of API specifications for a "shift left" approach and enforce and test API security using a positive security model.
Secure Your APIs Today
#1 API security platform

