Tutorials
OpenAPI (Swagger) Security Audit Report Explained
In our previous tutorial, we have created an API collection, and imported and audited an OpenAPI (Swagger) definition file. Now we are going to drill into the report and walk you through how to get the most out of it.
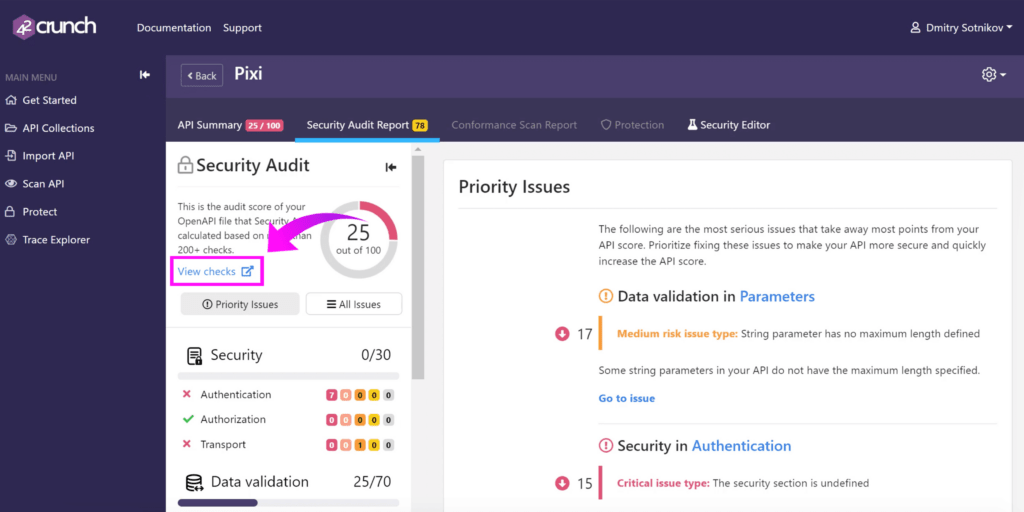
Viewing Checks
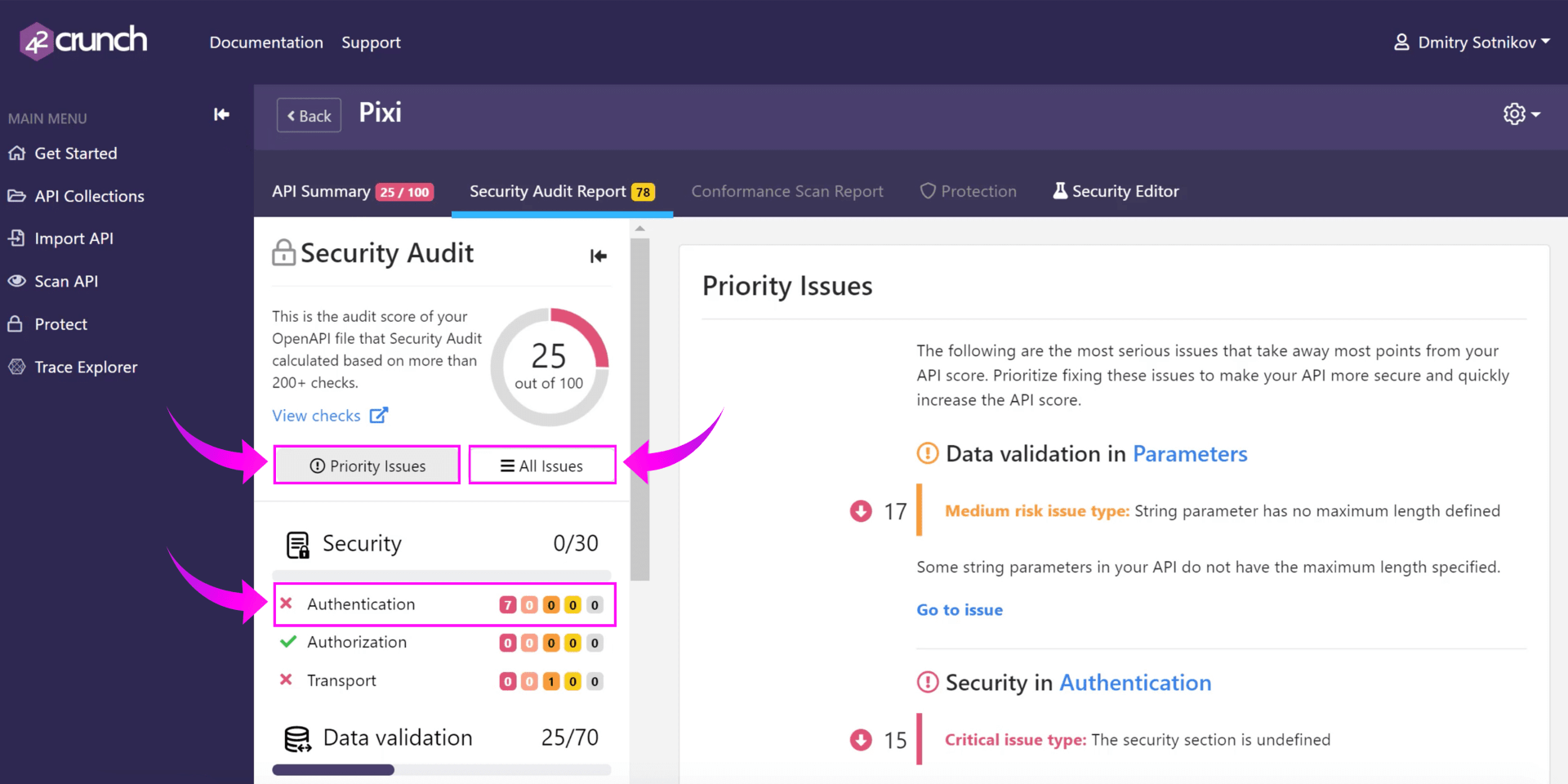
API Contract Security Audit is a static analysis of your OpenAPI (Swagger) file using OpenAPI Specification. We run 300+ checks on your API definition, and you can view all of them in our API Security Encyclopedia by clicking on View Checks within the dashboard.
Audit Score Overview
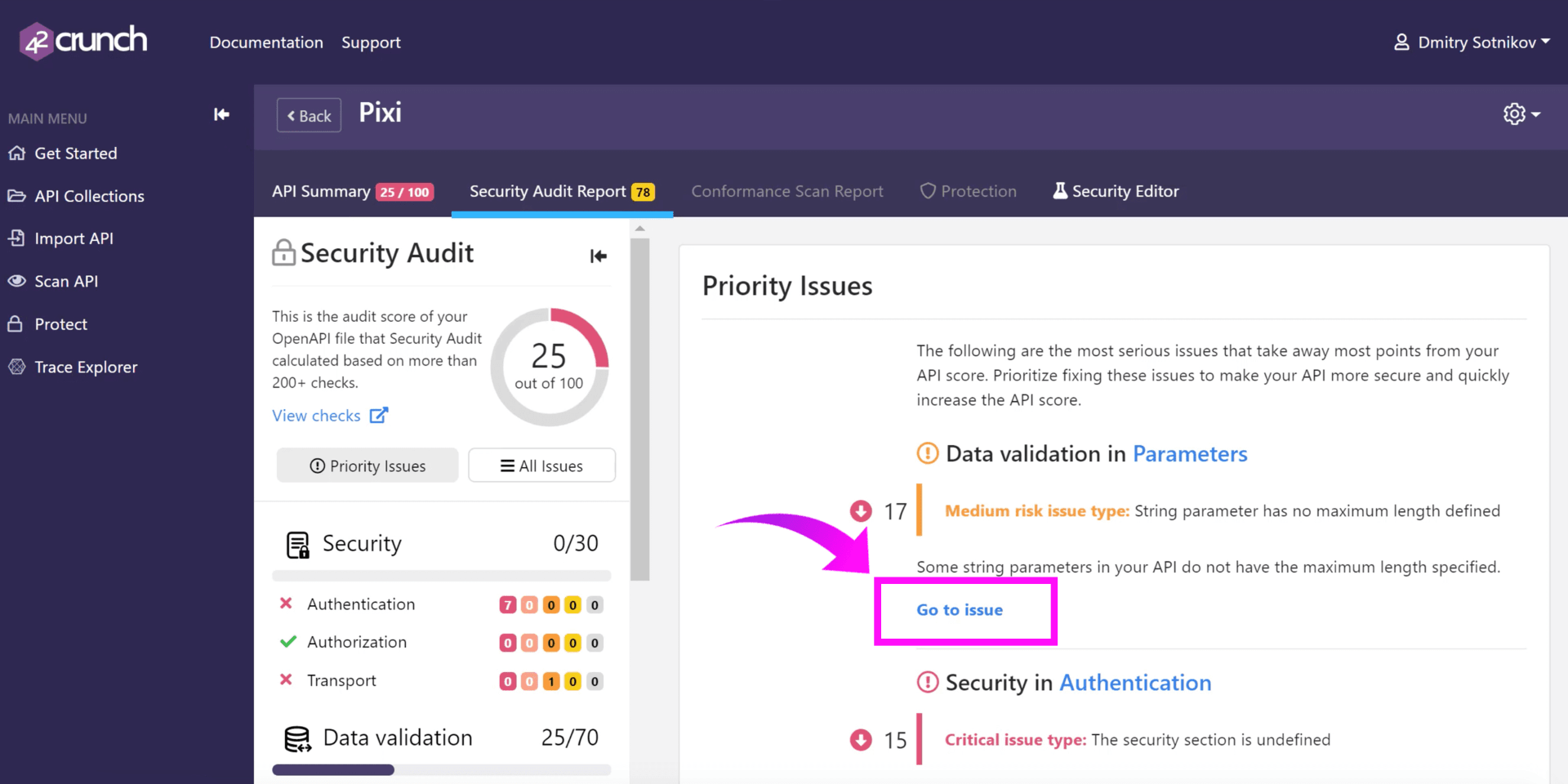
The audit score of your API is shown at the top of the report. The security audit is broken down into 3 sections:
- Security – Possible score of 30
- Data Validation – possible score of 70
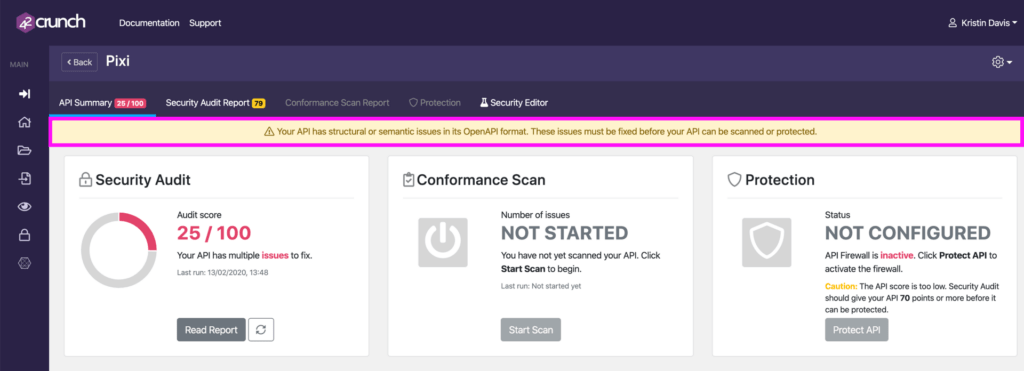
- OpenAPI Format – Formatting issues are not scored, but should be remediated first so you can proceed with protecting your API.
NOTE: If you import an API definition that is not a valid OpenAPI (Swagger) definition (that has issues in its format), you see a yellow warning at the top of the API summary page, and the found issues are marked with red in the report. To ensure accuracy of the audit, make sure that your OpenAPI (Swagger) definition is well-formed first.
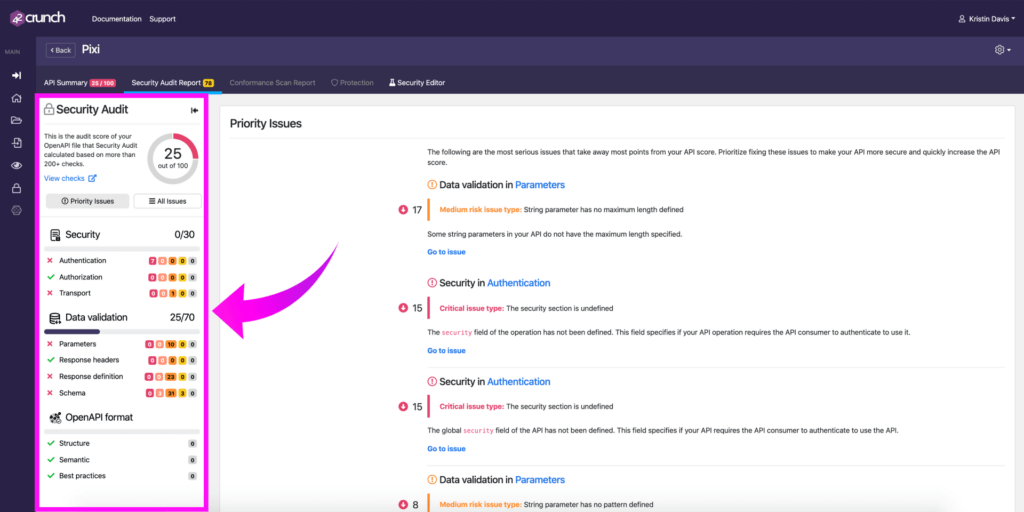
Navigating the Report
All actual security issues are scored based on the risk involved. The greater the risk, the higher the score (priority). You can filter issues by priority or category, or view all found issues as a list. You can also search for specific issues both in ‘All Issues’ and in each individual category.
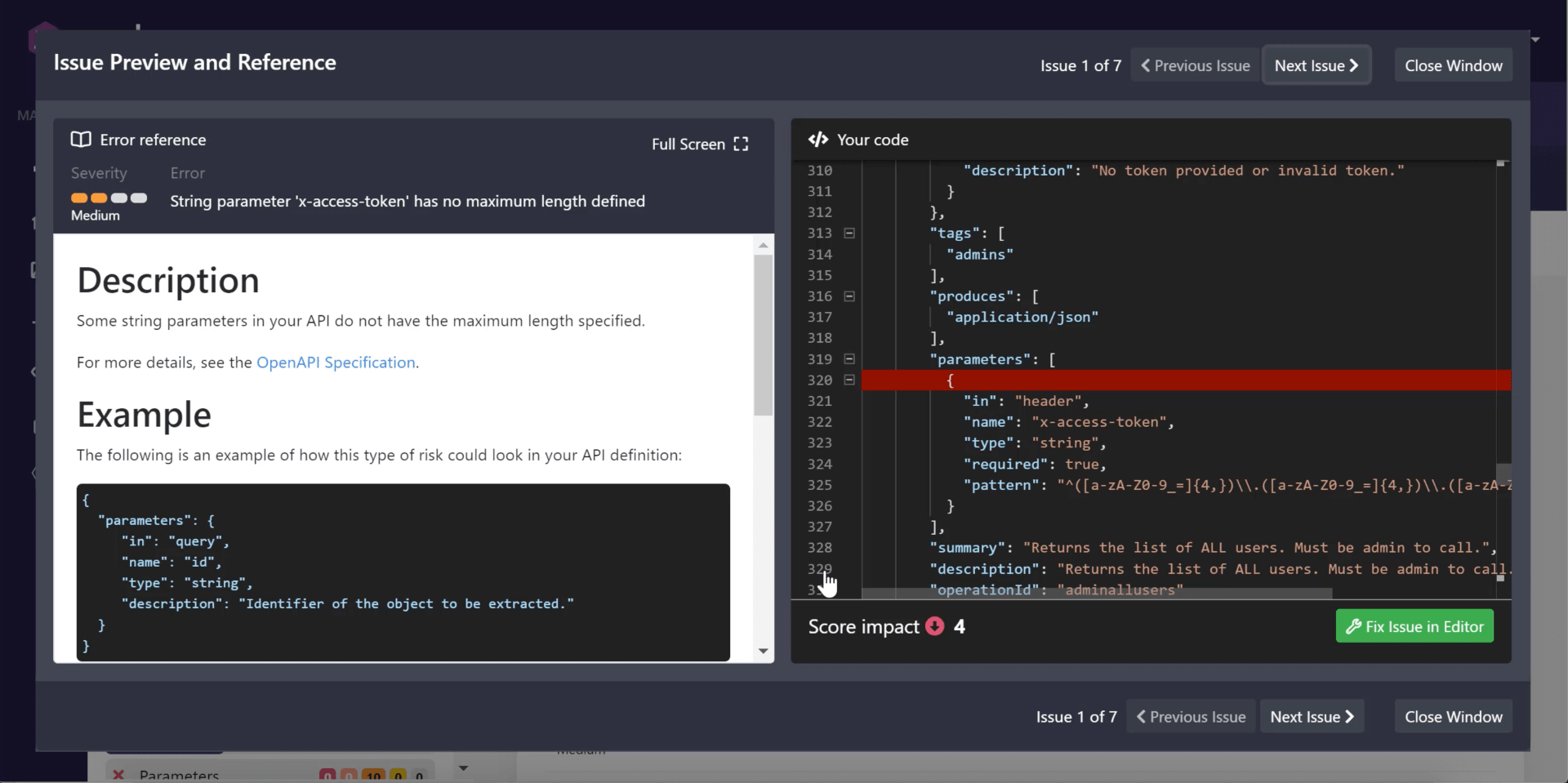
You can immediately start fixing issues from the priority list, or click into individual issues and remediate from there. Clicking on Go to Issue takes you to the place in your code where the issue occurs and shows you a description and remediation recommendations.