Tutorials
API Security Platform Overview
Overview of the 42Crunch API Security Platform, how to get started and the general dashboard layout.
Login and Dashboard
To log into the platform, go to https://platform.42crunch.com/login
A successful login takes you to your dashboard and the landing page of the platform. From here you can immediately start creating API collections, importing API definitions, or check your profile settings.
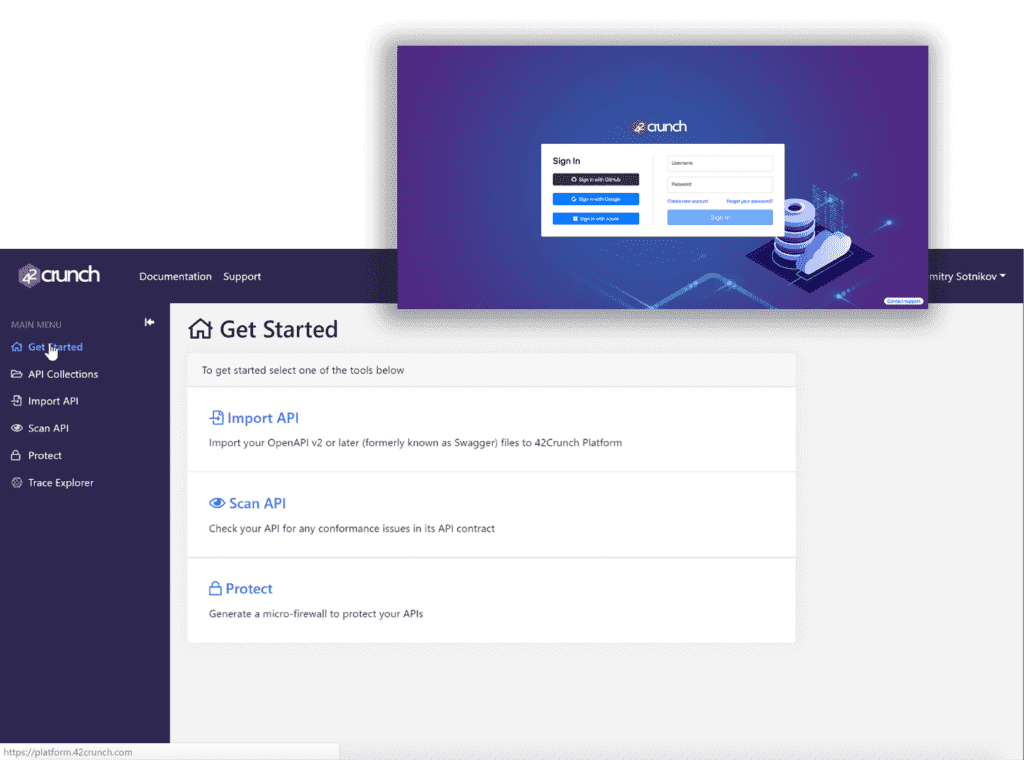
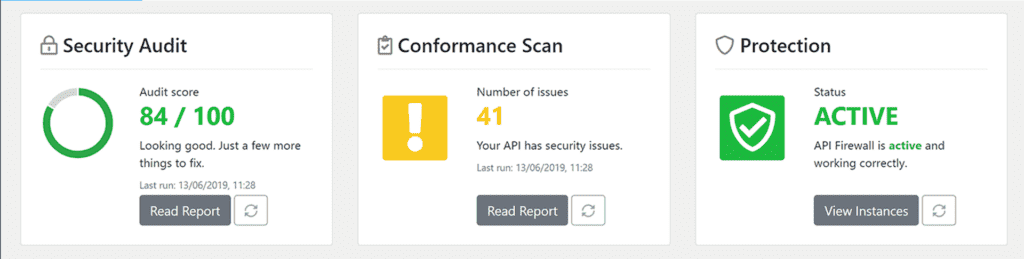
Platform Functions
A unique thing about 42Crunch Platform is that we give you a comprehensive solution that is applicable not only to runtime protection but to each and every step of the API lifecycle.
42Crunch Platform offers three main features:
- API Contract Security Audit: This is a static analysis of OpenAPI (Swagger) definitions, something that you would likely use during API design, development, and testing, or with your pull request reviews and your CI/CD pipelines.
- API Contract Conformance Scan: This is the dynamic testing of the actual API implementation. This function is very applicable in penetration testing, CI/CD pipelines and your test procedures.
- API Protection: This lets you tailor runtime protection for your API and put a micro firewall in the line of traffic to protect your live API endpoints from malicious attacks.
Navigation Basics
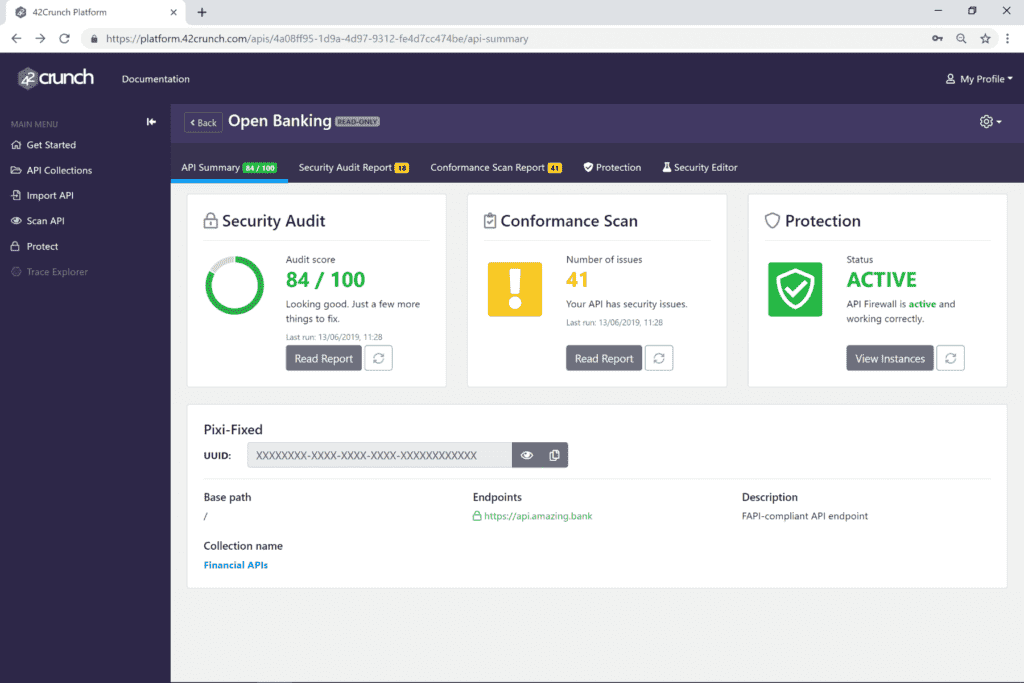
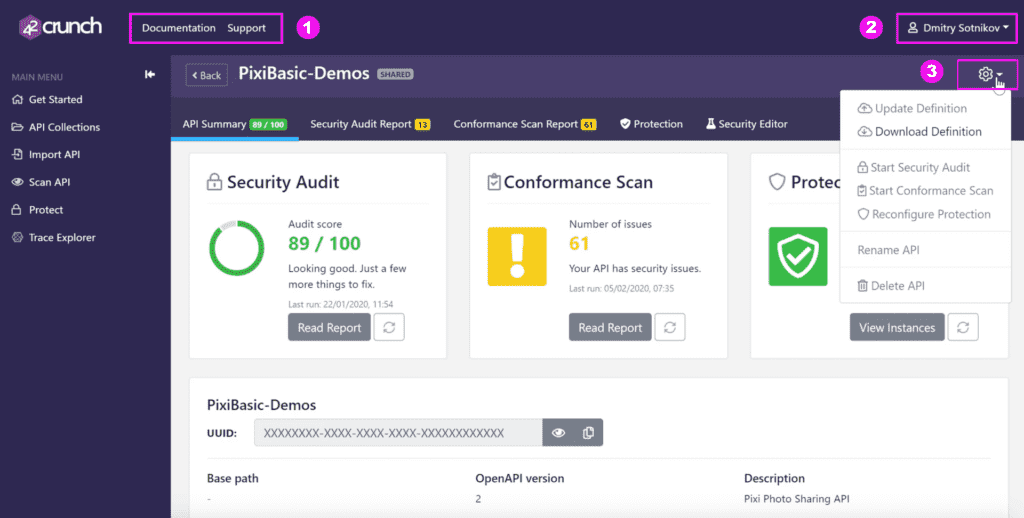
Navigation basics The following image shows:
(1) At the top left, you can find links to documentation and support for your convenience.
(2) At the top right, you can click your name to manage your profile or create API tokens for external integrations.
(3) The gear icon shows the actions you can perform on the API (or API collection) you are working on.
Getting Started with Collections
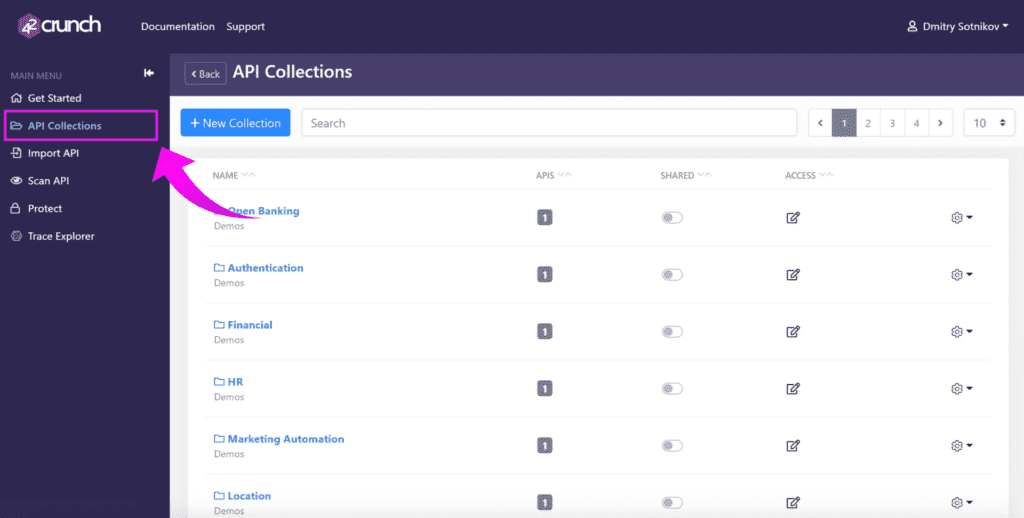
Getting started with API collections In 42Crunch Platform, APIs are organized in collections. You can create collections when you import API definitions, or even before that, just click API Collections in the main menu on the left. For example, you could group APIs into collections by department, project, or source code. You can control who has access to APIs across your company to allow for easier collaboration and reporting.