API Security Platform
Fix Your APIs Today, Prevent API Breaches Tomorrow
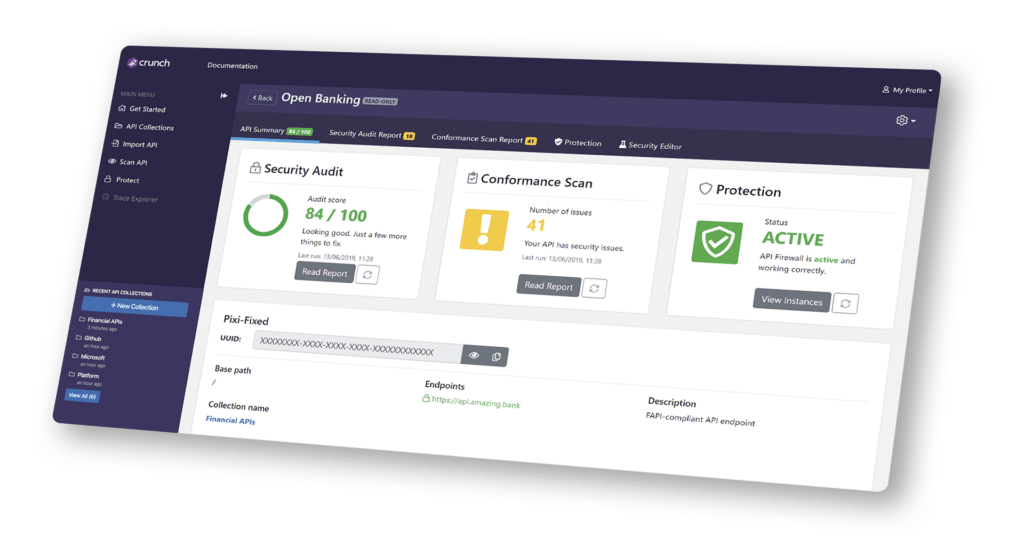
Enabling Continuous API Security
42Crunch enables a standardized approach to securing APIs that automates the enforcement of API security compliance across distributed development and security ecosystems.
42Crunch brings API semantic, code hygiene and data definition to all APIs. Security teams now gain oversight and governance of the policy enforcement throughout the API lifecycle.
Empower your developers to implement security as code in their workflow. 42Crunch is embedded in IDEs, code repositories & CI/CD environments.
Security is never the bottleneck. Enable your developers to focus on high-value work to improve and accelerate the delivery of world-class APIs.
Security audit and scanning become automated checks ensuring that insecure code never makes it to the master branch and production deployment. Runtime protection policies get automatically redeployed with each API change.
Traditional solutions generate an unacceptable volume of false positives. Eliminate noise and only see the issues that actually matter and need to be fixed.
Eliminate friction between development and security teams and automate protection to ensure that your API security program has unlimited scale.
Hundreds of Thousands
of Developers
Secure APIs with 42Crunch





42Crunch API Security Platform
Enterprises deploy 42Crunch to navigate the challenge of enforcing API security across a complex landscape of distributed development teams and multiple technical architectures. 42Crunch automates the enforcement of API security policies and standards across these development and security ecosystems. We help security take back control of API Governance and give development the tools they need to build safer APIs.

API
Governance
- Discover and catalog APIs automatically.
- Automate the building of API contracts from traffic and other sources.
- Integrated with development repositories.

Security Governance
& Compliance
- Standardized, secured API contracts.
- Centrally managed security compliance rules.
- Centrally managed runtime security policies.

API Security Testing
& Vulnerability Detection
- Empower developers with security tools with no false positives.
- Instantly calculate APIs security score against 300+ checks.
- Automate security fuzzing from API contracts.
- Deploy within any open-source or commercial CI/CD.

Runtime API Threat
Protection
- Automated configuration from API Contracts, with no manual rules.
- Detect & block shadow /zombie APIs as well as API-specific attacks.
- Standard, deployment-agnostic policies, working with any API Gateway.
- Connect to your favorite SIEM for combined threat intelligence.
Integrated into Developer & AppSec WorkFlows
Continuous security enforcement across IDE, CI/CD and at runtime.
How it Works
Our API Security platform leverages the OpenAPI Specification (OAS) to enable enterprises adopt a design and security first approach to protecting APIs. Security is designed and coded in at API design time and enforced automatically throughout the API lifecycle from design, development, testing, deployment and at runtime.
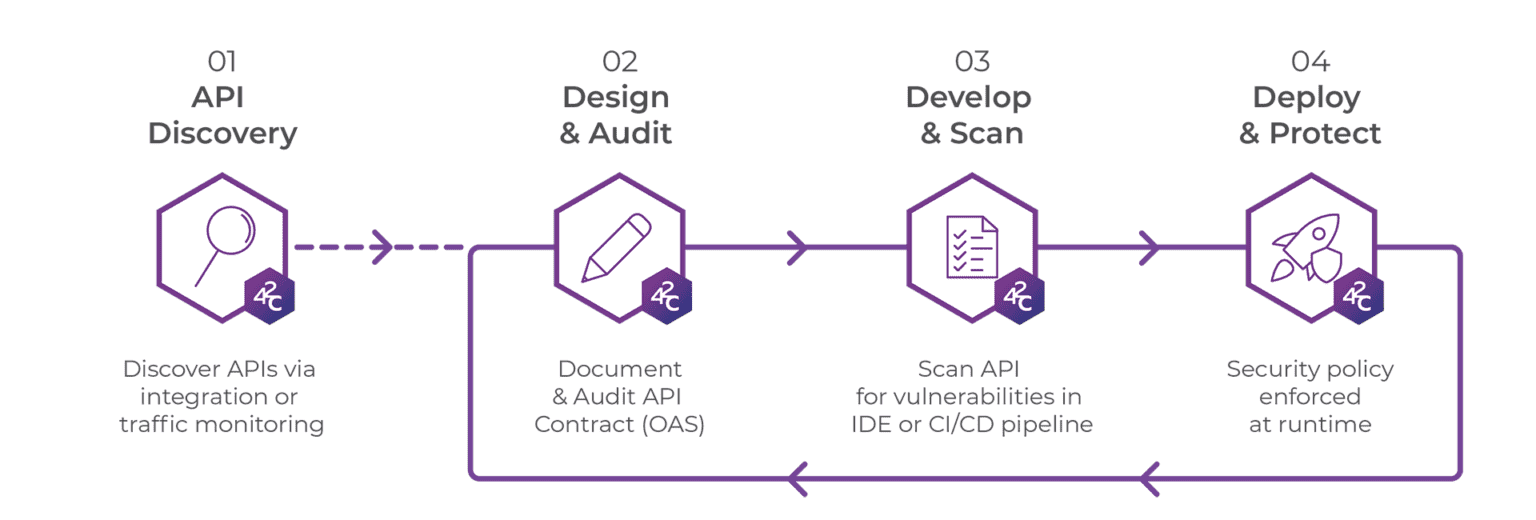
Get more detailed information on how our Developer-First API Security platform works.
Ready for DevSecOps
42Crunch is uniquely designed to enable a collaborative DevSecOps approach to API security. All teams: API architects, developers, QA, security, operations – get a shared view of API security, its shared definition, and shared understanding of what needs to be done to improve it. Combining shift-left with shield-right has never been so easy!
Security
Turn error-prone manual API security into fool-proof production deployment.
Deploy Anywhere!
Use 42Crunch to equally protect north-south and east-west traffic. Thanks to its low footprint, it can be deployed at scale on any container orchestrator such as Kubernetes, Amazon ECS or Red Hat OpenShift(®). 42Crunch also integrates with existing collaborative developer tooling such as GitHub, GitLab and, or Azure pipelines.

The overall score awarded to the 42Crunch API Security Platform is a 5/5 start - the highest rating I've ever given a vendor thus far.
Alissa Knight
Cyber Security Analyst
Darren Shelcusky
Manager Vehicle and Connected Cybersecurity
Ford Motor Company

Secure Your APIs Today
#1 API security platform
