Every day, new breaches show us that we still have a long way to go with API security. In order to protect APIs, enterprises need to take a holistic approach, which includes the following:
- Securing the infrastructure: OS configuration, network configuration as well as containers.
- Properly configuring application servers: enforce TLS 1.2/1.3, remove weak cipher suites, eventually enforce mutual SSL, use security headers, use secure cookies, use latest versions of frameworks/libraries, etc.)
- Defend against attacks by validating data: this includes JSON/XML validation, data/exception leakage detection, mass assignment protection, token leakage/forgery and in general OAuth/OpenID connect attacks protection.
- Ensure API payloads (messages) are encrypted and/or signed depending on data and operations sensitivity.
- Enforce authentication
- Enforce authorization (the #1 issue on the OWASP Top 10 API Security list is an Authorization problem!)
- Optionally implement non-repudiation for critical transactions
- Audit everything happening, at the system level and at the transaction level. This is critical for security forensics.
This list might seem long, but a locked-down Kubernetes-based architecture is no help if the application deployed on top of it lets you become an administrator with a single API call.
No one vendor is going to provide support for the entire spectrum: as an enterprise, you will need to compose several solutions to address all potential vulnerabilities. Items 3 through 6 above cover two fundamental aspects: API threat protection and API access control, as depicted in the diagram below.
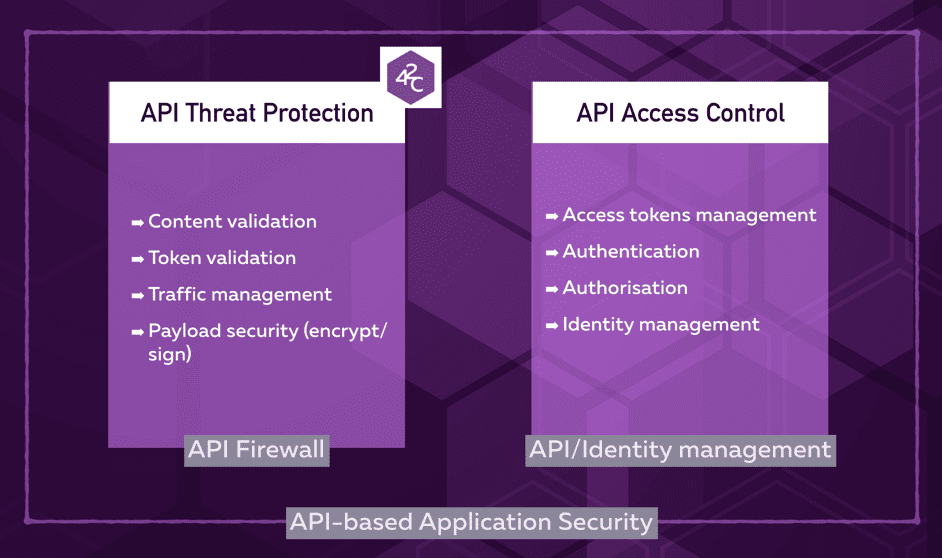
The 42Crunch platform focuses on the Threat protection aspects, while API Management and Identity Management focus on the authentication and authorization aspects.
Our solution complements API Management on multiple fronts:
- Introducing API Threat protection at design time: we help developers define a secured API contract in OpenAPI/Swagger at design time. In particular, we detect poor schemas, undocumented responses, missing responses types and poorly defined parameters and headers. Developers can use the tools offered by their API Management platform or dedicated tools to enhance the API contract description and obtain high security scores.
- Keeping API contract in line with API implementation: we ensure that the implementation matches the API contract, detecting early issues with data validation, data or exception leakage. Those 3 issues are at the core of 90% of API breaches. Developers can fix issues in the code or in API Management policies to comply with the security requirements.
- Eliminating the need to write individual policies by directly enforcing the OAS file constraints at runtime, therefore automatically protecting API from threats.
- Providing individual, scalable protection: each API can be protected by its own API firewall, thanks to a very low footprint (20 megs Docker image) and sub-millisecond latency.
- Providing out of the box protection against stolen tokens, forged tokens and OAuth-based attacks.
- Providing out of the box protection against malicious bots, preventing this traffic from even reaching the API gateway.
- Automatically injecting recommended security headers
By adopting a solution like 42Crunch, enterprises can focus their API Management platform on access control: governance of API keys and OAuth/OpenID tokens, user authentication, and resources authorization. 42Crunch tools and services ensure they can detect security misconfigurations and potential vulnerabilities early in the API lifecycle and moreover automatically. The entire process of auditing the OAS file, scanning the APIs for issues and deploying protections becomes part of the enterprise CI/CD pipeline, allowing security to scale as the number of APIs increases.
Our goal is to make API threat protection as agile as development and fully part of the lifecycle: development has changed in the past decade, becoming more agile, even more with the adoption of loose coupling architectures and Kubernetes. Manual security processes such as code scanning, security testing and security rules deployment quickly become roadblocks if they are not fully automated and moreover, initiated by developers.
If you have already deployed API management platforms, you will benefit greatly from the 42Crunch platform as it adds automated threat protection to your developers tools belt and helps your security teams detecting potential vulnerabilities early in the API lifecycle.
Request a platform demo today to discover how our platform can help you boost the API security capabilities of your API Management solution!



