Tutorials
BitBucket Pipelines API Security Audit Extension
In this quick tutorial you’ll learn how to add static security testing to your REST APIs in Bitbucket with the 42Crunch REST API Static Security Extension. Prerequisite: Make sure you have a 42Crunch API Security Platform account. You can register here: https://platform.42crunch.com/register
Create API Token for the pipe
You must add an API token that the pipe uses to authenticate to Security Audit.
- Log in to 42Crunch Platform, and click your profile.
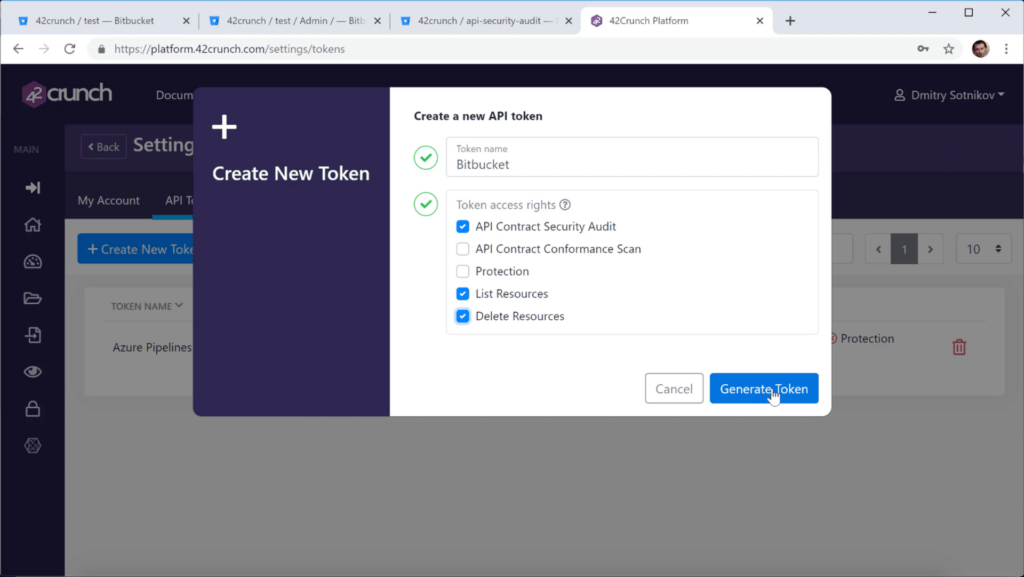
- Click Settings > API Tokens, and click Create New Token.
- Enter a unique and descriptive name for the token, such as CI_CD token.
- In token access rights, select API Contract Security Audit, List Resources, and Delete Resources.
- Click Generate Token.
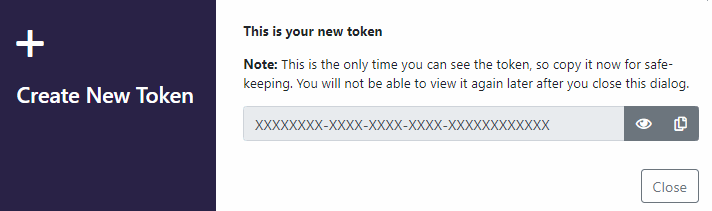
- Copy the token value, you will need it when you configure the task on the pipeline.
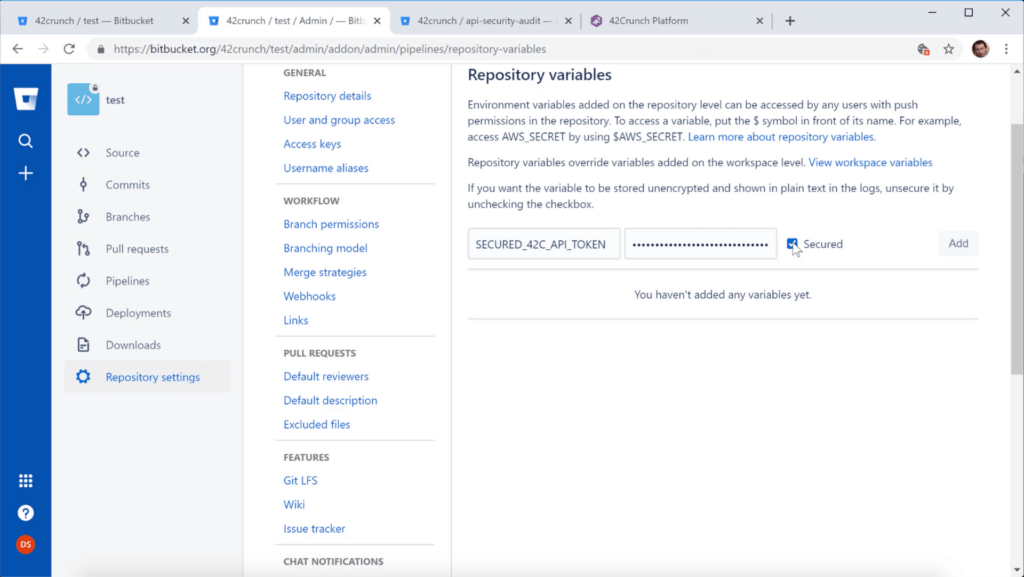
Add a Bitbucket variable for the API token
Before you add the pipe to your Bitbucket pipeline, you must add the API token you created as a secured repository variable.
- Log in to your Bitbucket account, and go to your repository.
- Click > Repository settings > Repository variables.
- Enter the following: as the variable name, as the value, and make sure you select Secured: Name: SECURED_42C_API_TOKEN, Value: The value of the API token you created
- Make sure Secured is selected, and click Add.
You have now created the variable that your pipeline can use to authenticate to Security Audit.
Add the pipe to your Bitbucket pipeline
To run the pipe, you must add it to your Bitbucket pipeline.
- Log in to your Bitbucket account and go to the pipeline you want.
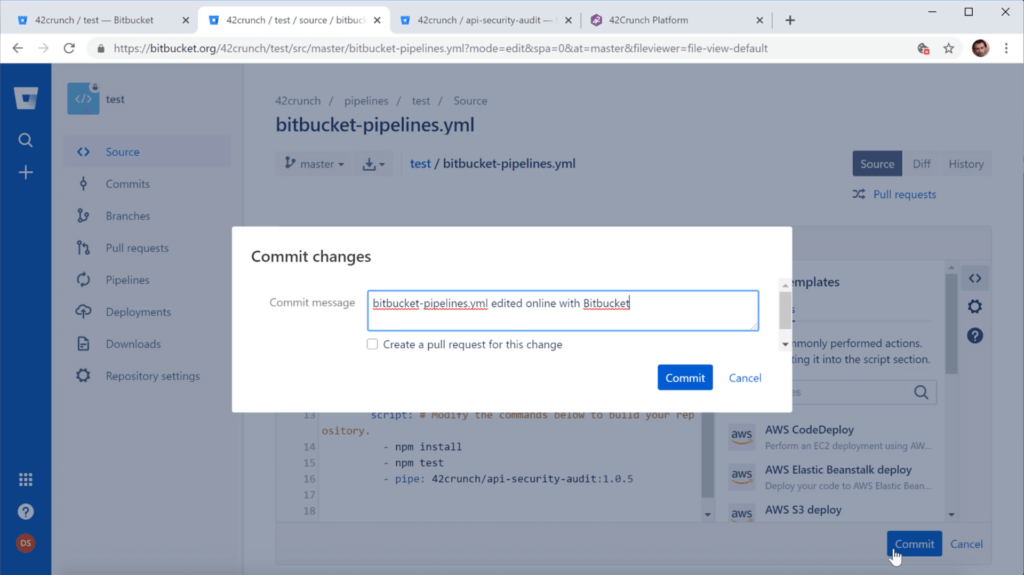
- Open the pipeline configuration file bitbucket-pipelines.yml for editing
- Under script, add the following line where you want to add the pipe: - pipe: 42crunch/bitbucket-api-security-audit-pipe:1.0.5
- Click commit!
REST API Static Security Audit
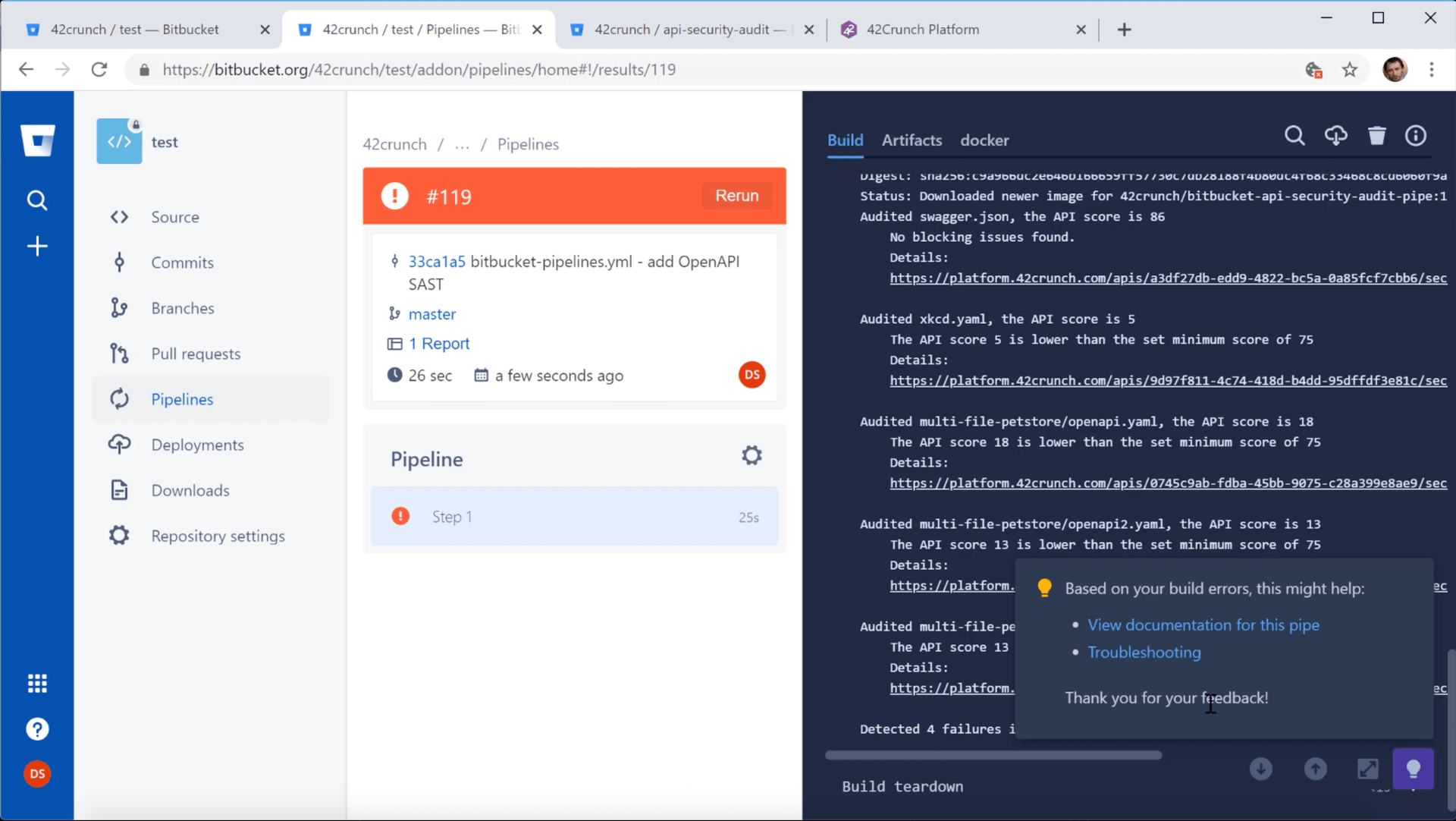
The pipe will either succeed or fail depending on the minimum score. The summary of the run in the pipeline reports provides you further details on how the job went.
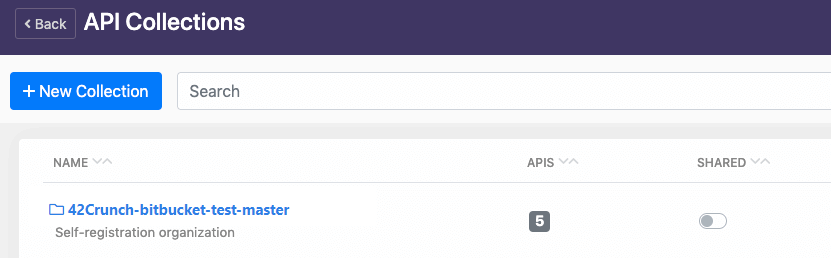
The pipe uploads all discovered OpenAPI (Swagger) definitions to the specified API collection in 42Crunch Platform.
The report of the run include a link to each discovered API. You can click on the link to view the detailed audit report of the corresponding API in 42Crunch Platform.