Tutorials
API Protect Micro API Firewall Reports and Troubleshooting
You’ve seen how 42Crunch can protect your APIs and microservices – now let’s review reporting.
Viewing Transaction Logs
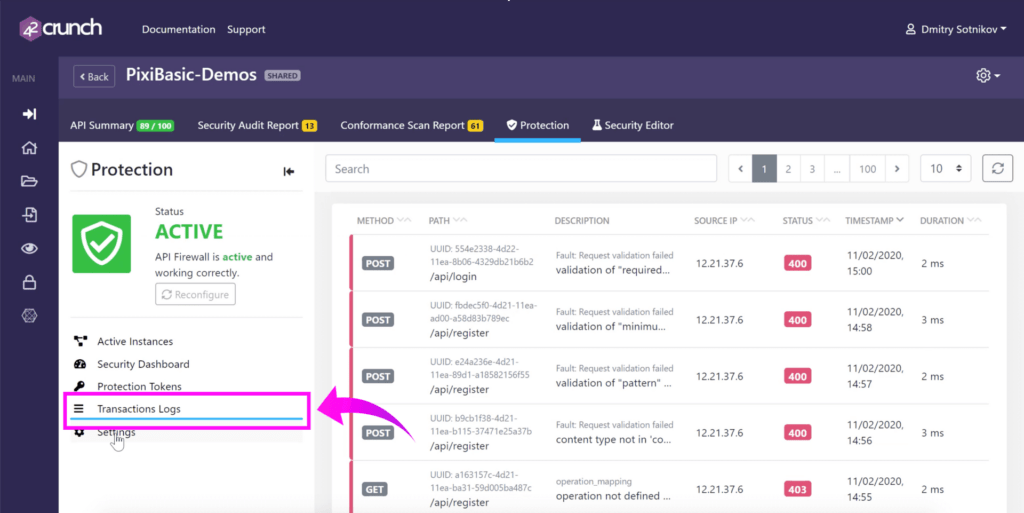
At any time, you can click on transaction logs to view all failed transactions found by the conformance scan and review the full list.
Look up a Specific Error
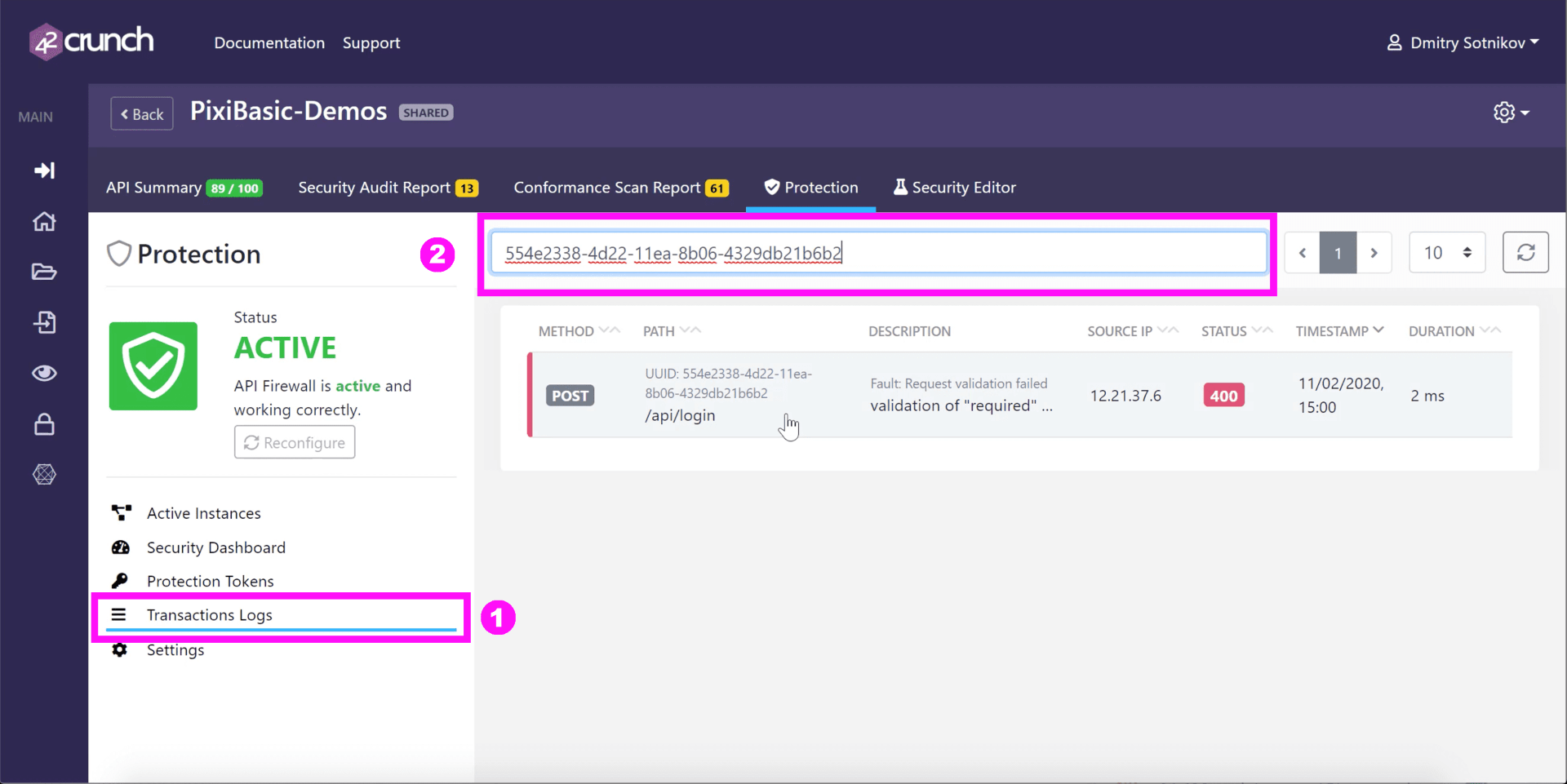
So one thing that I want to show first is how you can troubleshoot and see that specific transactions that get blocked. Sometimes you can have legitimate users and maybe your partners, your other teams who might have been using your APIs incorrectly – and might have started relying on some sort of hacks of your APIs and using the APIs in a way that you wouldn’t expect. And they might call you and complain that something that used to work, no longer works. All you need to do is ask them for that transaction ID.
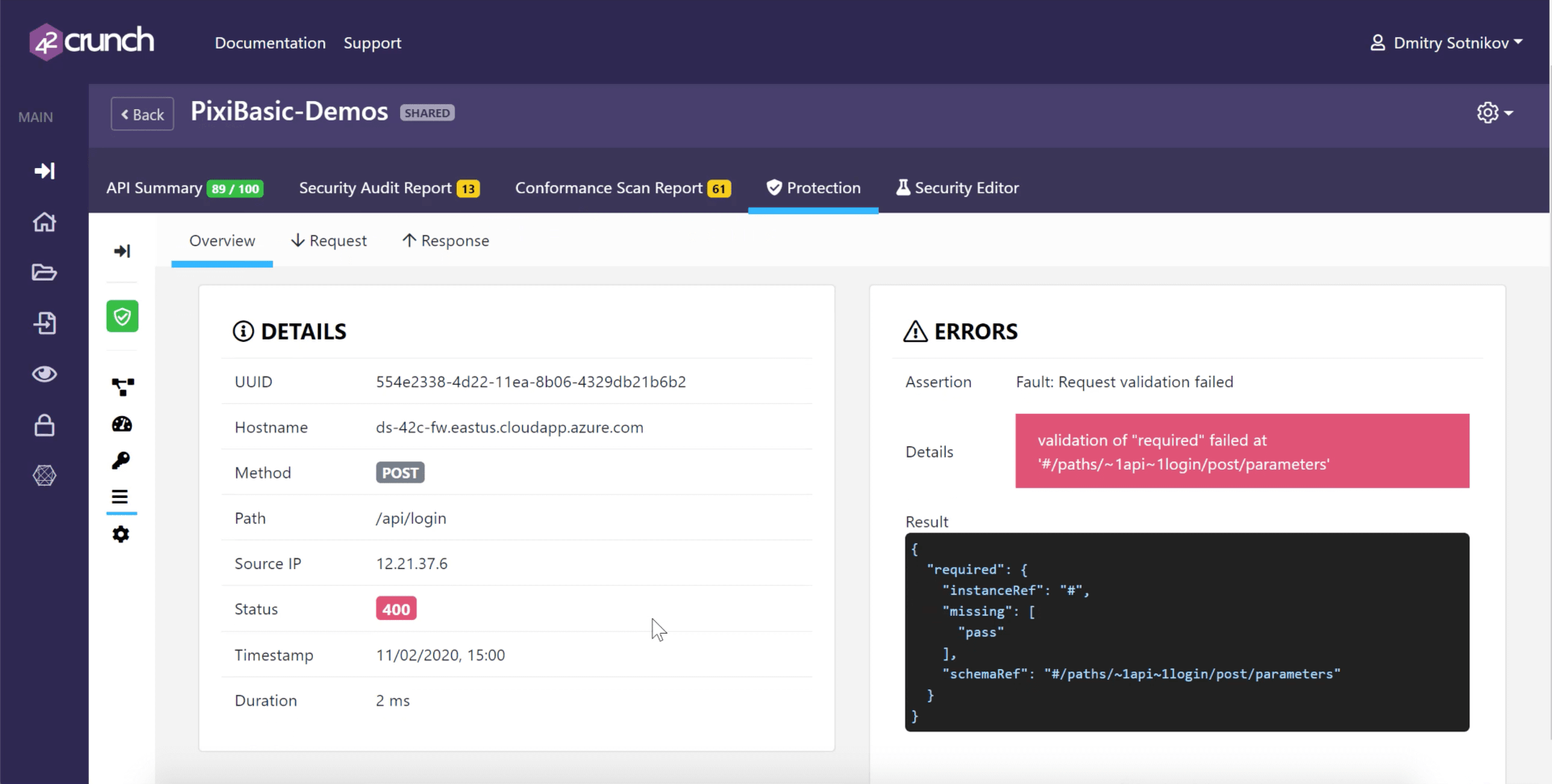
Now you can easily go into the 42Crunch console and use that ID to look up the specific transaction and drill down into the details of what went wrong.
Click on Transaction Logs, then paste the ID into the search bar. You will see what exactly happened, what exactly failed and why. You will get detailed information for the requests coming in, and then if response was blocked – what happened to the response.
Non-blocking Mode
There’s a setting to run the firewall in nonblocking mode. This is something that you can use when you don’t yet want to enable the protection, but you want to start getting reports on all the calls that are outside of the contract. So maybe if you are not comfortable yet to start enforcing the protection and you want to just figure out who is using your APIs incorrectly outside of a contract, you can run it in non-blocking mode and see those calls before you enable the protection.
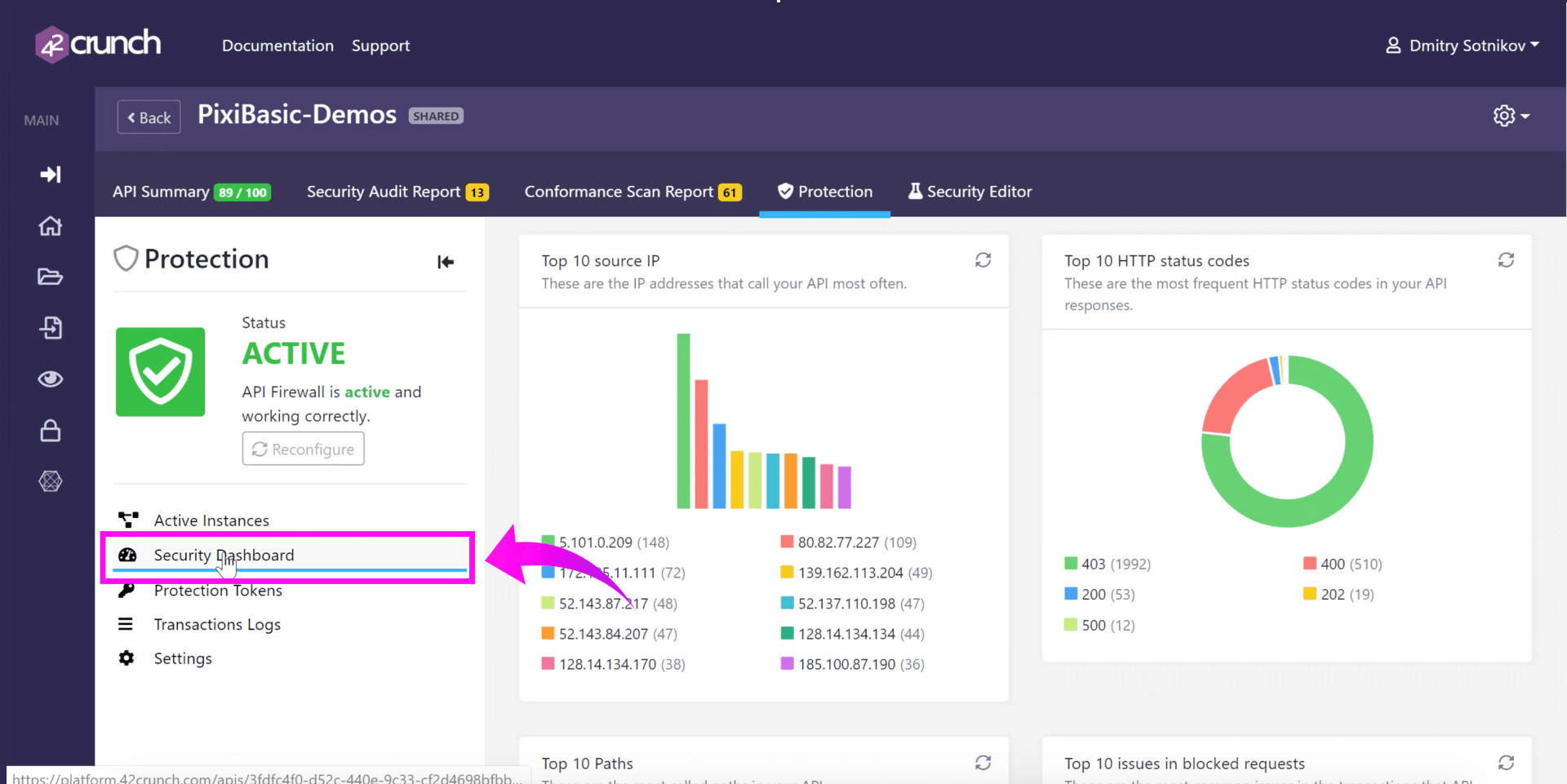
Security Dashboard
You can click on ‘Security Dashboard’ to view overall reporting to see how your APIs are being used.