Tutorials
OpenAPI (Swagger) Security Audit on the 42Crunch Platform
Now that you have had an overview of the platform, let’s get started by importing an API for security audit.
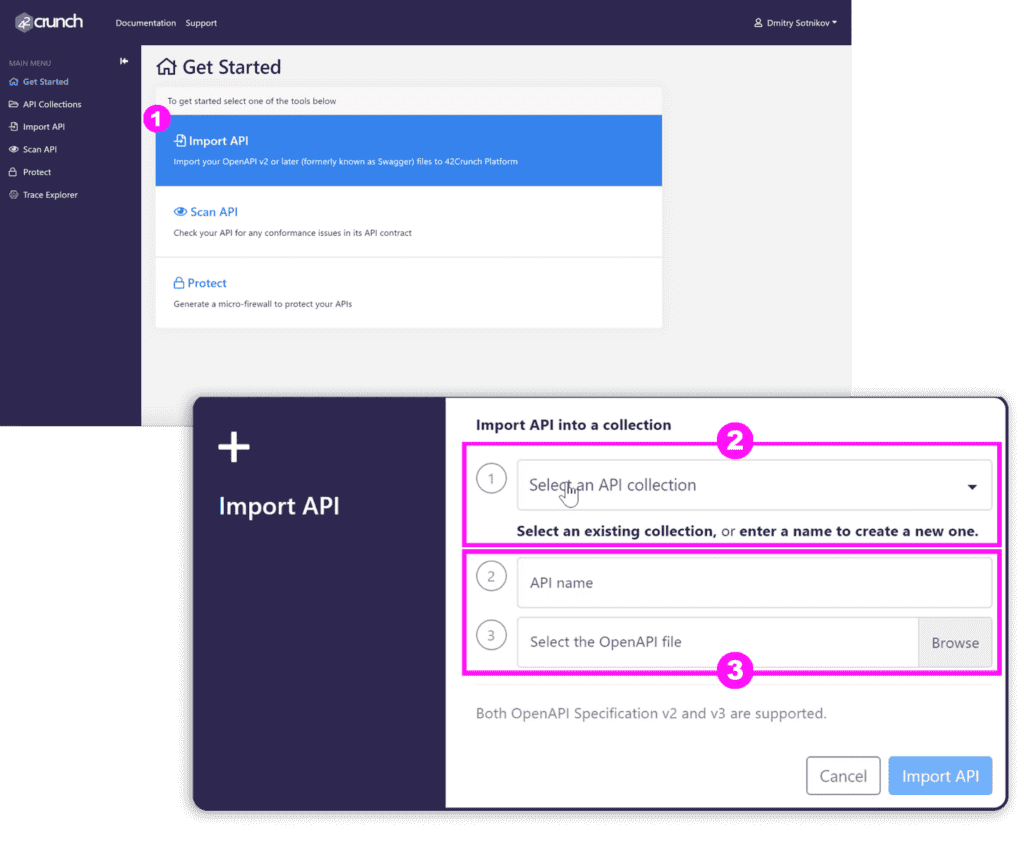
Importing APIs
To import an OpenAPI (formerly Swagger) definition, click Import API (1) to upload your JSON file. These files contain all the basic information and documentation on how your API functions.
As mentioned in the platform overview tutorial, (2) APIs are grouped into collections. If you have not yet created a collection, you can do it when you upload the file, or choose an existing collection. (3) Click Browse to pick the JSON file you want to upload. The API name is pre-populated based on the name of the file, but you can change it if you want.
Click Import, and you are on your way to securing your API contract!
Tip: To automate importing OpenAPI / Swagger definitions, you integrate it with your CI/CD pipeline.
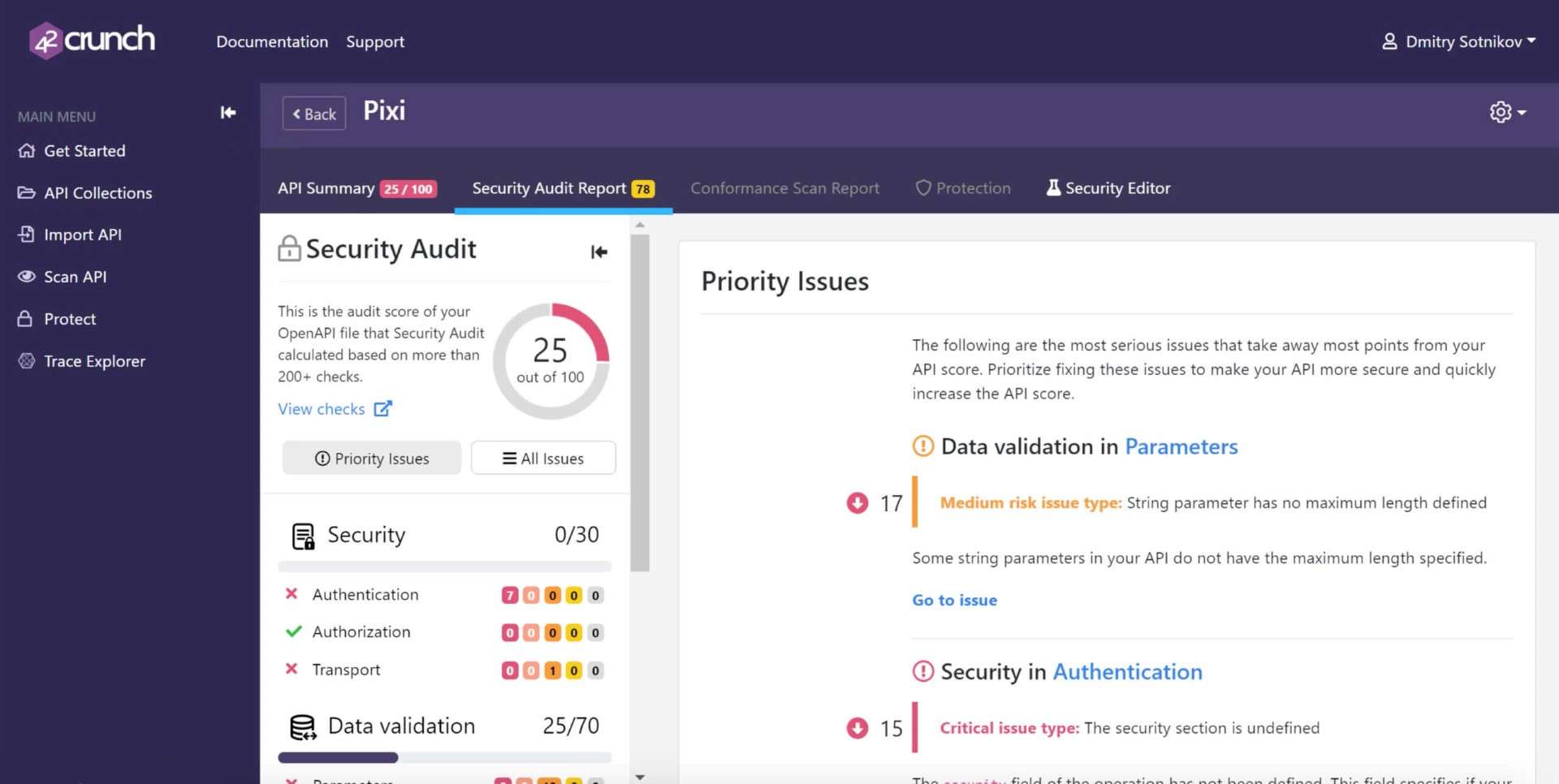
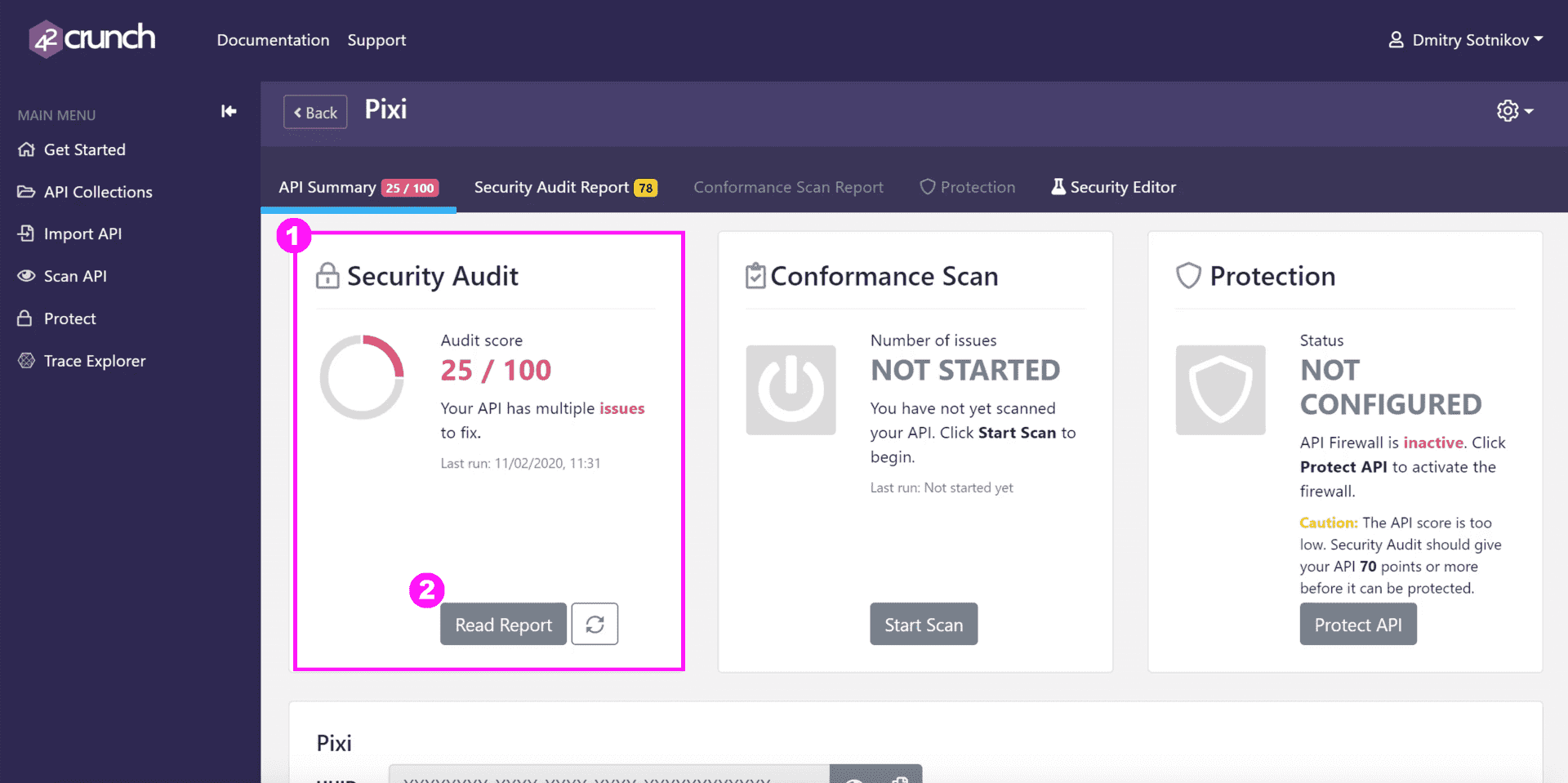
Audit Results
When you import an API definition, API Contract Security Audit runs 300+ checks on it and returns a report in seconds. The audit is based on the security best practices of the industry standard, the OpenAPI Specification. Your API gets a score from 1 to 100 based on how secure it is (1) To view the details of the audit report and the found issues, click Read Report (2).
The audit report outlines all the issues in the well-formedness and security of your API definition, ranks the security risks by severity, and shows you how you can fix the found issues.
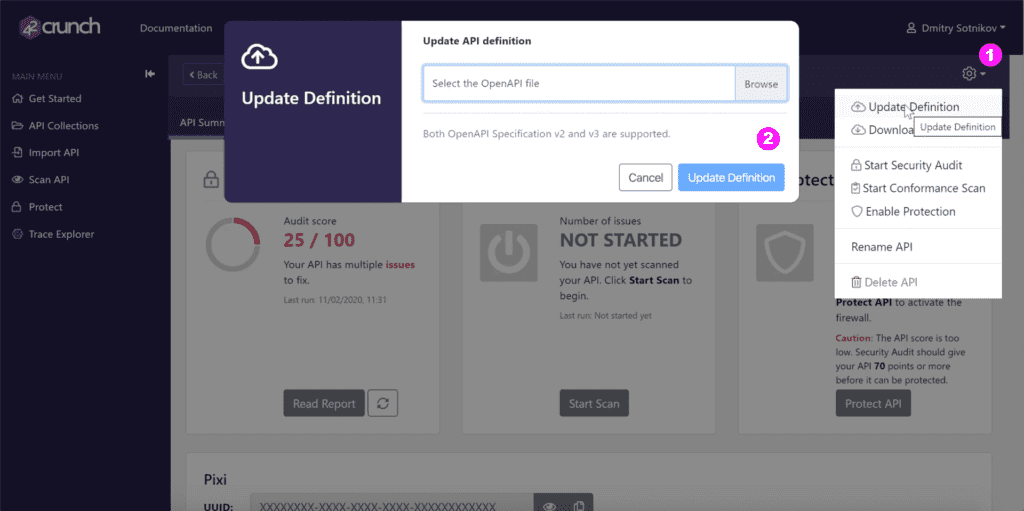
Updating API Definitions
If you change an OpenAPI (Swagger) definition you have already uploaded to 42Crunch Platform, you can update the changes to the platform as well. Click the gear on the right, and select (1) Update Definition. Click on Browse to pick your file, and click Upload Definition (2).
Tip: Again, to automate importing OpenAPI / Swagger definitions, you integrate it with your CI/CD pipeline.