The OWASP API Top Risks listing identifies three different Authorization challenges
Coding issues relating to Authorization configuration failures continue to present a significant challenge for development and security teams building and protecting APIs. Just read any issue of our fortnightly APIsecurity.io newsletter and you’ll discover that Authorization-based breaches are at the root of a large percentage of the high-profile attacks. Authorization, in its various flavors, presents challenges because any misconfigurations or vulnerabilities can lead to unauthorized access and harmful data breaches.
In a recent 42Crunch webinar, “Top Things you Need to know about API Security” with Isabelle Mauny and Dr. Philippe De Ryck, we explored why Authorization warrants 3 different entries in the OWASP API Top 10, why it is difficult to get right and how organizations should go about implementing Authorization safeguards.
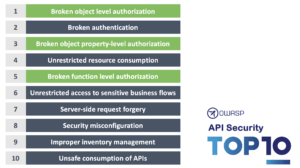
Figure 1. Authorization entries in the OWASP API Top 10
Authorization Compliance is Complicated
Many APIs are characterized by layers of complexity which inevitably leads to a complicated rules logic. Ensuring that this logic is accurately implemented and determining what the authorization rules should be can be challenging. It is even doubly difficult to check for compliance once the API has been deployed as there is the added time pressure of racing to review and remediate any holes, before the API is potentially attacked. All an attacker requires is one hole from which to build his attack from. This is why building logic into the APIs during the development phase is a recommended best practice.
Philippe De Ryck observed though that when developers are quizzed by security about how they can prove that their Authorization checks work and how they were implemented there tends to be a lot of head scratching and finger crossing. He suggested two ways in which security and engineering developer teams can successfully implement these checks.
- Make authorization auditable
- Define the authorization rules in the OpenAPI contracts and ensure that the APIs enforce that contract and its rules.
Make Authorization Auditable at Scale
Authorization is undoubtedly a critical aspect of your overall API security posture. But without the ability to audit authorization checks in your security policies you will have great difficulty in identifying whether developers have implemented the appropriate checks in the correct places.
The best way to do this is to integrate security measures early in the development lifecycle by giving your developers easy to use API audit and scan testing tools that run in their IDEs and help them implement Authorization best practices as they build their APIs. In parallel, you also need to give your security teams real-time oversight via these tools from within the CI/CD pipelines to ensure that the authorization requirements are being adhered to.
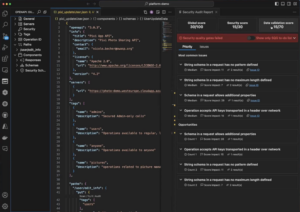
Figure 2. 42Crunch audits & scans Authorization checks inside the development IDE
OWASP Authorization Issues
The OWASP API Authorization challenges are identified next and how 42Crunch can help companies address them.
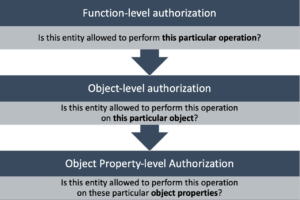
Figure 3. Different levels of API Authorization: Functional, Object and Object-Property
Broken Object Level Authorization (BOLA)
BOLA relates to a flaw or weakness in the implementation of object-level authorization within an API. It means that the API doesn’t adequately verify and enforce the permissions associated with a specific object, allowing unauthorized users to access or modify it.
Risk: Attacker substitutes the ID of their own resource in the API call with an ID of a resource belonging to another user. Lack of proper authorization checks allows attackers to access the specified resource.
Fix:
- Implement authorization checks with user policies and hierarchy
- Don’t rely on IDs sent from the client. Use IDs stored in the session object instead
- Check authorization for each client request to access the database
- Use random non-guessable IDs (UUIDs)
-
Implement a robust test framework to specifically test for this vulnerability type leveraging 42Crunch.
Broken Object Property Level Authorization (BOPLA)
This vulnerability occurs when the API fails to properly enforce authorization controls at the property level. It is a combination of two previous OWASP risks, Mass Assignment and Excessive Data Exposure.
Risk: It means that users could gain unauthorized access to or modify specific properties of an object.
Fix:
- Never rely on client to filter data
- Review all responses and adapt to what API consumers need
- Define schemas of all the API responses
- Don’t forget about error responses
- Identify all the sensitive or PII info and justify its use
- Do not automatically bind incoming data to internal objects – Explicitly define all the expected parameters and payloads – Set readOnly property to true in object schemas for all properties retrieved through APIs that should never be modified – Precisely define the schemas, types, and patterns you will accept in requests at design time and enforce them at runtime.
Broken Function Level Authorization (BFLA)
BFLA refers to a security vulnerability where the API fails to properly enforce access controls on specific functions. Users can perform certain functions or actions for which they do not have the appropriate permissions.
Risk: API relies on the client to use user level or admin-level/privileged APIs as appropriate. Attackers figure out the “hidden” admin API methods and invoke them directly.
Fix:
- Do not rely on the client to enforce admin/privilege access
- Apply deny all access by default
- Only allow operations to users based on appropriate role
- Implement properly designed and tested authorization
Conclusion
There are tools and techniques designed to mitigate security vulnerabilities at the earliest stages of design and development so that you reduce the risk and cost associated with late-stage Authorization security issues. The 42Crunch API security platform makes it easy for developers and security teams to continually identify and remediate Authorization vulnerabilities and misconfigurations before deployment.
Further Reading:
Webinar: Top Things you need to know about API Security
Datasheet: Protecting the Enterprise: How 42Crunch Remediates the OWASP API Top 10 Security Risks



