LOSING MY RELIGION: Successful and unsuccessful approaches to API Security in a global enterprise – A take on Ford Motor Company’s approach to API security and the journey to enforce security compliance while ensuring productivity of thousands of developers managing thousands of APIs.
The Cybersecurity Snowball Effect
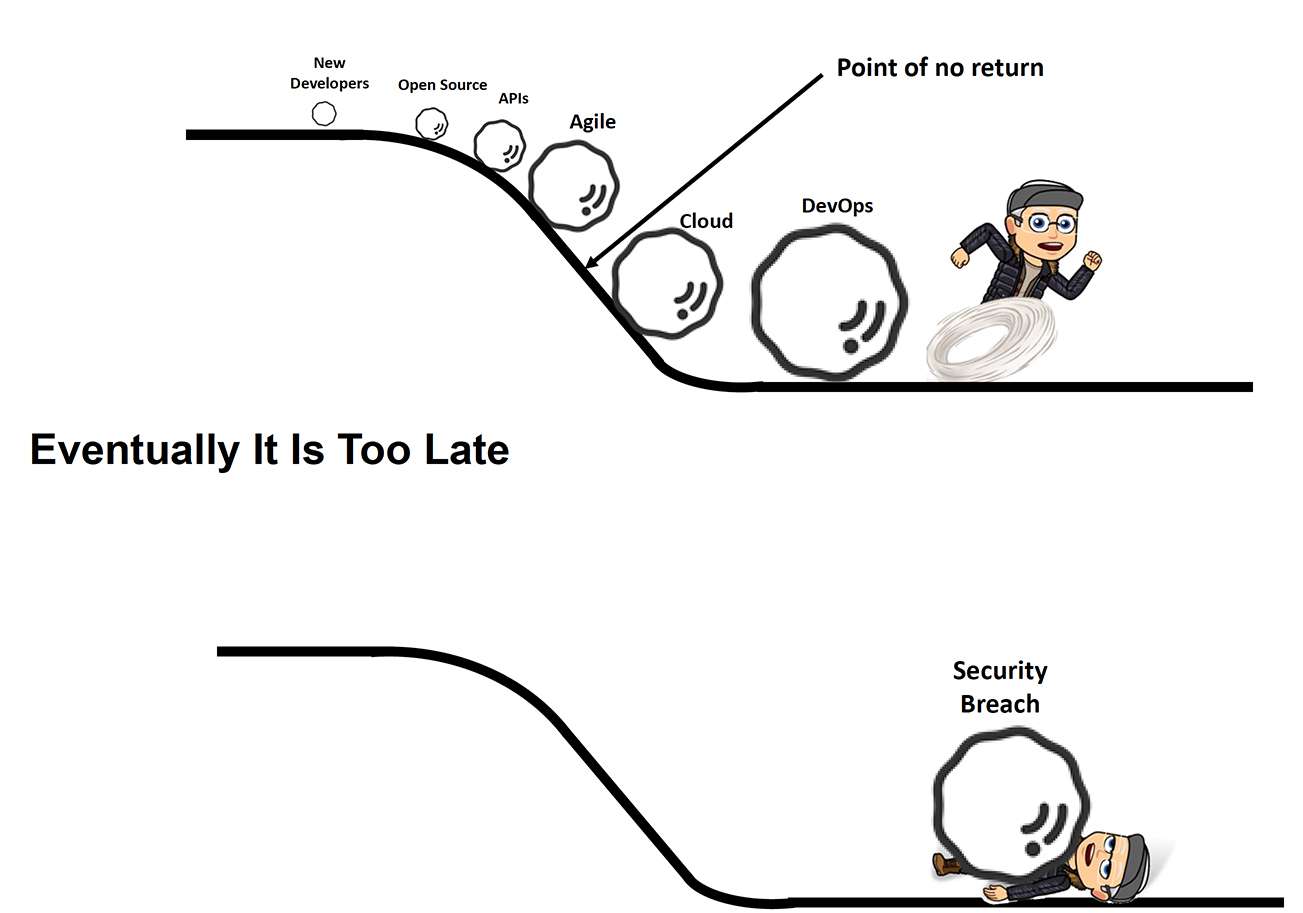
With development Communities and product teams, there are many things that have come together – everything from new developers, the introduction of open source, new APIs, agile development techniques, the cloud, DevOps, DevSecOps…etc. Eventually, if you don’t manage this, it will catch up with you and you’re going to hit a point of no return. Whether you’re a small company, a medium sized company, or a large enterprise, ignoring and not addressing these issues we’ll end up in a security breach (hit by the snowball)! Many people may not realize that cybercrime is more profitable than the global drug trade. Now, consider that fact – and APIs are important because criminals are going to go to where the data is.
API security is still relatively new. The OWASP API Security Top 10 was released at the end of 2019. So, we’re only a little over a year into having these well-defined API security vulnerabilities as an industry that software professionals can now begin to address.
So, the question remains: how do you prevent an API security dumpster fire?
Giving it the Old College Try
Before we talk about what works let’s address a few failures that we have seen along the way.
Whack-a-Mole Approach – We find a problem; we fix a problem. If you’ve ever played the game, whack-a-mole, you know you hit it with a mallet and another one pops up and over time their speed and number escalates as you try hitting them – desperately trying to keep up. At some point you realize there’s no hope of winning the game because the moles are going to come quicker than you can ever whack them down. Same with the snowball analogy, you’ll never have enough snowballs to attack all the threats. This approach may work for a little while, but it will catch up with you and a breach will happen.

We’re Just Going to Monitor Everything – Like the boy who cried wolf, security professionals are prophets of woe until someone sees a wolf. We all know wolves exist and they are dangerous, but until they attack, the guidance of security professionals is often reduced to hyperbole. While you can monitor everything, you’ll never have enough monitors or people to respond to the monitors and your signal to noise ratio tends to be very high. Like the fable, the boy who cried wolf, people may stop believing you because of all the false positives.

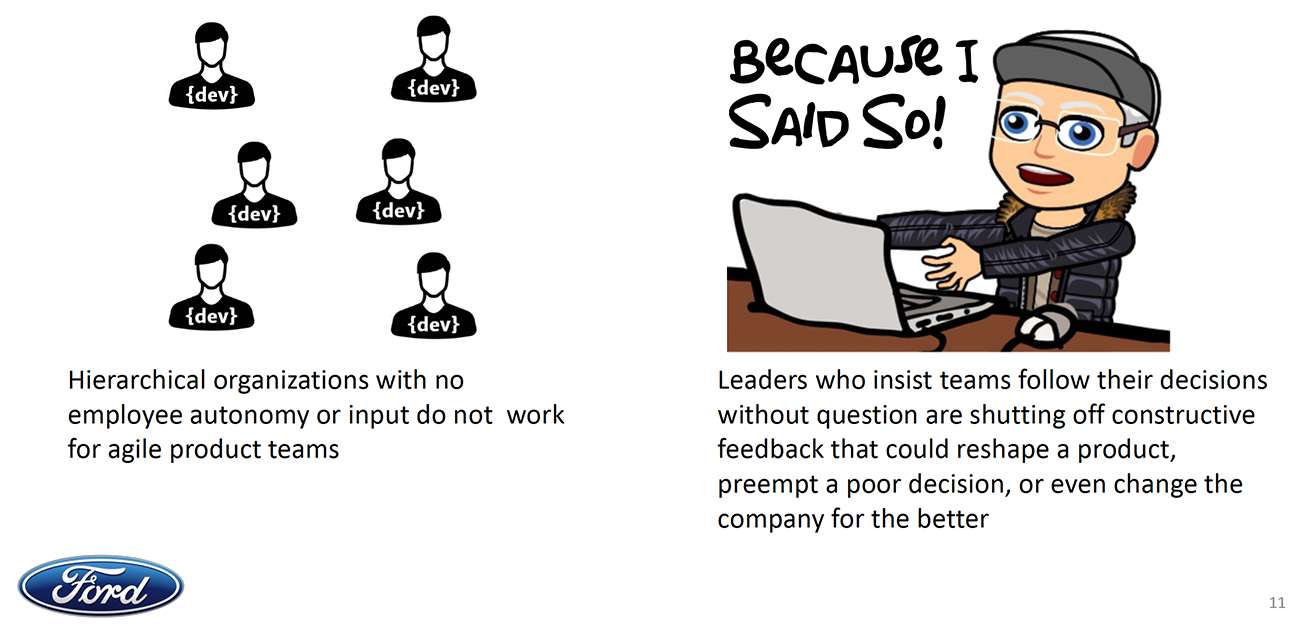
Mandating Policy and Standards – Policy and standards are good, but they aren’t enough. They’re only effective when employees understand them and use them in the development process, meaning it’s not only baked into the development process, but also part of the pipeline and release. If it is something that is out of the day-to-day norm, then it quickly becomes forgotten. If this is not automated, then it will fail.

The Command-and-Control Approach – So the next approach is the top-down management, the command-and-control approach. “Do this because I said so!” It can work to a point, but realistically leaders who insist that their teams follow their decisions without question can lose a lot of learnings and constructive feedback that could make products better. This type of approach can also cause an imbalance for agile product teams.
Collaboration: People, process and technology
API security is a balancing act. There is a people aspect, process aspect and technology aspect. If those are out of balance, you’re going to fall off your stool and the bad guys out there will be ready to attack. API security is not a security problem, it’s a shared business responsibility. The people, processes and technologies must work together to manage risk. This is very important. If you don’t do that, you’re going to waste a lot of money. If you focus on the technology and ignore the people and processes, you will fail. If you focus on the processes, ignore the people and technology, you will fail. If you focus on two of them, you’ll still fail. It’s the balancing of all three of these things that create the foundation for a successful API security program for an organization of any size.
For security to be fully successful through the balancing act of people, process and technology, you must find ways to eliminate manual work wherever possible and augment manual efforts with a shift-left approach to automate everything starting at design time. It’s only through automation and enabling DevSecOps that the team can maintain their velocity and deliver a secure, quality product.
The 5 Steps to Strengthening API Security Posture

Know your inventory – If you don’t know what’s out there, in a large enterprise such as Ford Motor Company, things can get lost pretty easily. Teams can go out on their own and go rogue and do things with great intentions, but all of a sudden you find out there are a lot of security problems. So absolutely get a handle on your API inventory.
Audit your sensitive APIs – Make sure that you perform a security audit on your most sensitive APIs. This way you can find and remediate security issues before an attacker does.
Attack the OWASP API Security Top 10 – Do everything you can to address the OWASP API Security Top 10. If you are not familiar with them you can click on the below to learn more:
- A1: Broken Object Level Access Control
- A2: Broken Authentication
- A3: Improper Data Filtering
- A4: Lack of Resources & Rate Limiting
- A5: Missing Function/Resource Level Access Control
- A6: Mass Assignment
- A7: Security Misconfiguration
- A8: Injection
- A9: Improper Assets Management
- A10: Insufficient Logging & Monitoring
Trust but verify – You have to trust your teams to do the right thing, but we’re human. People are under pressure to hit a deadline and mistakes can be made. Sometimes things just happen. You want to make sure that you can verify it. So if something happens it can be found and remediated immediately.
Coordinate disclosure and bug bounty – Don’t assume security knows everything. Invite the good people to help you find bugs. You’d be amazed at what you can learn from that!
LOSING MY RELIGION: Successful and unsuccessful approaches to API Security in a global enterprise
View the webinar page here for more associated materials and information.
Resources
Learn more about 42Crunch API Security Platform
Are your APIs secure? Try a free audit at apisecurity.io: https://apisecurity.io/tools/audit/
Learn more about how 42Crunch addresses the OWASP API Security Top 10



