The OWASP API Security Project released an updated version of the OWASP Top 10 for APIs last month. In the intervening years since the first edition was published in 2019 API security has risen to become arguably the most pressing area of focus for CISOs and Heads of Application Security today. Certainly, at 42Crunch we have seen increased customer demand across all industry verticals and indeed the rate of uptake of our developer-friendly API security tools continues to increase with over 850,000 downloads to date.
In last week’s webinar on the new 2023 list of API Security vulnerabilities, Colin Domoney examined the changes made to the latest list of API Security vulnerabilities, discussed what the implications of these developments might be for enterprises and explored specifically how 42Crunch can help remediate these threats.
He also posed several questions to the audience of cybersecurity architects, API developers and DevSecOps folks, the results of which are presented below and undoubtedly will help to further focus security practitioners’ minds on the issues that matter most.
Something Old, Something New
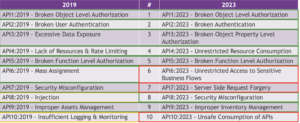
There has been some movement in and out of the Top 10 listing this year with authentication and authorization remaining at the top, new items to address scalping and fake account creation and server-side request forgery being added and some more general, non-API specific threats moving out.
A new item called “Unrestricted Access to Sensitive Business Flows” has been added to manage the prevalence of bots accessing APIs. It is essential to identify sensitive business flows in order to shield them against bot-based attacks. This reinforces the need to highlight – if it were needed – the importance of not only secure coding but also secure planning and design when building a new application.
Earlier this year we hosted a webinar with Jim Manico investigating Server-Side Request Forgery (SSRF) as we had identified a trend of more SSRF driven attacks on API-based applications. The OWASP Foundation was obviously on the same wavelength as it comes straight in at No. 7 this year
Whilst Injection and insufficient logging and monitoring have dropped out of this year’s Top 10 listing it does not mean they have disappeared as legitimate threats. Rather they belong to categories that apply broadly across the security spectrum and are not just API-specific. The rationale underlying this year’s additions is that the vulnerability should have a more API-centric focus.
No. 1 Concern
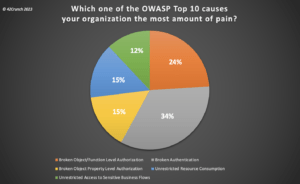
API-based applications are increasingly complex with thousands of endpoints and user hierarchies. Consequently, authentication and authorization are now arguably the biggest challenge for API security, and it’s no surprise that 4 out of the top 5 items are related to these areas. The polling question we put to our audience reinforces this observation. Our poll showed that Broken Authentication is the number one concern for enterprises today.
Upstream Provider Visibility
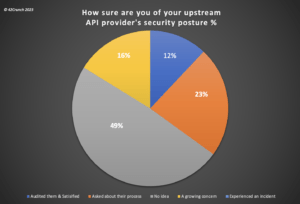
We also surveyed the audience on their oversight of their upstream API providers’ security postures. Nearly 50% of firms admitted to having “no idea” as to the security stance of their providers which should set alarm bells ringing amongst all security teams. As companies seek to protect their own internal and externally exposed APIs, they also need to be confident that their partner providers are applying the same level of diligence to services they expose for third-party consumption.
Conclusion
It would seem that companies are increasingly sensitive of the need to strengthen their API security defenses and that the OWASP API Top 10 listing helps advance the industry’s understanding of those challenges. However, as evidenced by the results of the question we posed to the audience, there is still room for improvement. Much done, much to do!
Something Old, Something New – OWASP API Security Top 10 in 2023




