Blog
Knowledge Series on API Security and API Security Best Practices
Bridging the API Security Gap – The Perception and Reality of API Security
What is the API Security Gap? A recent report from Akamai as covered in the apisecurity.io newsletter, corroborates earlier findings from a report we commissioned of EMA Enterprise Management Associates into enterprise adoption patterns of API security technologies. Both studies indicate that while there is a broad recognition […]
The Radware WAF Vulnerability: When Unexpected Input Bypasses Security
In issue 272 of APISecurity.io, we cover news of a significant vulnerability in Radware’s Web Application Firewall (WAF). The incident demonstrated how unexpected input could slip past the WAF’s defenses, allowing malicious requests to reach backend systems. One standout example involved a GET request with a body payload, […]
Securing APIs in the Age of GenAI: Test Before You Connect
How to secure your APIs from GenAI and LLM based attacks Generative AI (GenAI) and Large Language Models (LLMs) are transforming the enterprise landscape, enhancing customer and employee experiences with unprecedented efficiency and insight. The recent McKinsey Global survey on AI reports that 65 percent of respondents say […]

Discovering your APIs – How to achieve a complete API Inventory
API usage and traffic continues to grow thanks to the massive amount of SaaS and other web-based services that power our modern economies. However, as businesses become more distributed the landscape of their API estate and microservices has become increasingly complex. These vast and potentially ungoverned API landscapes present attractive targets for attackers and challenging […]
The Scourge of SQL Injection for APIs
In a report published in May 2024, cybersecurity firm Eclypsium outlined key vulnerabilities discovered in the F5 Big IP Next device. It’s another sobering reminder of the challenges faced in securing APIs when a highly regarded security company like F5 launches a new flagship product with all-too-familiar vulnerabilities like SQL injection and SSRF. Among the […]

What’s the best way to test an API for vulnerabilities? RTFM
If you’re a child of the 80s like me, you may have had the distinction of being the only one in your house who knew how to program your VCR. My motivation was strong. Clarinet lessons were interfering with my favorite show, the A Team. I was the one in the family who handled most […]
Buckle Up and Protect your Ride. The Importance of API Security for the Connected Vehicle
Last week 42Crunch and VicOne, a Trend Micro subsidiary, announced a unique and vitally important partnership for the automotive industry. Our partnership is the first of its kind to address the mission critical role API security plays for automotive manufacturers as the software driven vehicle becomes an increasingly vulnerable attack surface for rogue actors. Automotive: […]

How to Improve Developer Productivity and API Security Posture
Automate API Documentation and Security Analysis The proliferation of APIs has made them an attractive target for bad actors, so organizations need to adopt a multi-layered approach to protect their APIs. This starts with API design and progresses to the deployment and production runtime phases. To implement API security from the early stages effectively requires […]

Addressing API Security Regulations in Financial Services
Introduction APIs are disrupting almost every industry vertical, and nowhere is their impact more profound than in the financial services industry. Whether helping modernize legacy systems or creating entirely new business opportunities through innovations such as OpenBanking, APIs are the lifeblood of the financial services industry. At the same time, there is increasing scrutiny on […]
So, your API has been Breached, Now What?
Last week I had the privilege of presenting some real-world API security case studies at the annual API Summit in Austin, Texas. On foot of several requests, I have summarized in this post some of the key steps an enterprise should undertake, once they discover that their API has been compromised. Dissecting the API Security […]

How to Protect your APIs from Broken Authentication and Unrestricted Resource Consumption
In a follow-up to our recent blogpost which explored the OWASP API Authorization risks, this week we share highlights of our webinar which featured Philippe De Ryck and Isabelle Mauny talking about the Authentication challenges encountered when protecting your APIs. They explored just how potentially dangerous the combination of the two OWASP API Top 10 […]
How to Protect APIs from OWASP Authorization Risks: BOLA, BOPLA & BFLA
The OWASP API Top Risks listing identifies three different Authorization challenges Coding issues relating to Authorization configuration failures continue to present a significant challenge for development and security teams building and protecting APIs. Just read any issue of our fortnightly APIsecurity.io newsletter and you’ll discover that Authorization-based breaches are at the root of a large […]

How 42Crunch and Microsoft are Solving the API Security Challenge
42Crunch and Microsoft have partnered to provide continuous protection for APIs Recently 42Crunch and MIcrosoft announced a partnership to address the number one security issue challenging organizations today, namely the large and growing attack surface represented by APIs. Application security practitioners have come to realize that application security tooling like SAST/DAST and Web Application Firewalls […]

Analyst Report: Review of Partnership Between 42Crunch and Microsoft
This analyst report prepared by Dr. Edward Amoroso, CEO of Tag Infosphere Inc, offers a review of the recently announced partnership between cybersecurity vendor 42Crunch and Microsoft. Introduction The recently announced partnership between 42Crunch and Microsoft, integrating 42Crunch’s API security solutions 1 with Microsoft Defender for Cloud 2, marks a significant advancement in the field […]

How to Embed API Security Testing into the Development Lifecycle without Delaying Production Rollout
This is the first in a 3-part series of blogs exploring how 42Crunch assists enterprises with API security compliance. In her seminal blogpost, “Shifting Security to the Left” Shannon Lietz explains how including security testing earlier in the development lifecycle makes for longer-lived and more resilient software. The principles she advocates for are also what guides us at 42Crunch..

3 Steps to Successful API Security Compliance
CISOs and application security teams are faced with the challenge of enforcing API security compliance without delaying the development lifecycle or the delivery of new services. Often thought of as a bottleneck to rapid API delivery, there is now a wide acceptance of the key role security must play at all stages of the development […]

Why most API Security solutions have not delivered on the hype
Many early adopters have chosen to tackle the API security problem with traffic analysis tools that use AI/ML to discover known and unknown APIs and identify suspected attacks. Yet these companies are now telling us they’re inundated with false positives, and feel no closer to addressing the core issue of having vulnerable APIs.

The OWASP API Security Top 10 Has Been Updated – How Are Companies Reacting?
The OWASP API Security Project released an updated version of the OWASP Top 10 for APIs last month. In the intervening years since the first edition was published in 2019 API security has risen to become arguably the most pressing area of focus for CISOs and Heads of Application Security today. Certainly, at 42Crunch we […]

Mind the Gap! How API Security Testing Tools Complement API Gateways for Enhanced API Security
“I want security, yeah Without it I had a great loss, no now Security, yeah And I want it at any cost …” (Otis Redding, 1964) Otis Redding may well have been singing about the love for another in these famous lines, but taken literally, his message will resonate with any company that has recently […]

Why 42Crunch’s MISA Certification is Important for API Security
42Crunch is the first API Security platform vendor to join the Microsoft Intelligent Security Association (MISA). By combining Microsoft Sentinel’s intelligent analytics with 42Crunch’s API design and run-time security controls enterprises gain a holistic view of their API security program.

Empathy for the API Developer
Colin Domoney from 42Crunch, in his recent article on DevOps.com, addresses the disconnect between development and security teams and explains the key challenges facing developers in creating secure API code. Better understanding of the challenges on both sides can help create greater empathy which in turn can help foster greater collaboration. “..Security teams have always […]
An Introduction to API Security
Isabelle Mauny from 42Crunch takes a high level look at the different problems facing APIs today and gives some recommendations in her article on APIscene.io The idea of this article is to serve as an introduction to API security. We’ll look from a high-level view at all the different problems that are stacking up around […]

When Shift-Left is more than a marketing campaign
Earlier this month I had the chance to join my new colleagues from 42Crunch at our all-hands in Ireland and I couldn’t be more excited that there’s something special that we’re building here. Setting aside that Cork and Kinsale are some of the prettiest places I’ve ever visited, I was able to see how passionate […]

Sua empresa não tem alternativa: Proteger as APIs da forma correta passa a ser uma obrigação
O grande susto Um amigo comentou comigo um episódio interessante: Telefonaram para ele dizendo que era um canal de nível oito de seu banco, confirmando dados como endereço, nome de mãe e pai, cônjuge, filhos etc, dizendo que existiam transações suspeitas, e que a conta dele havia sido invadida e ele precisava ligar urgentemente para […]

Lessons learned from the Spring4Shell vulnerability
Recently we published an article on the log4shell vulnerability targeting log4j, in which we explained how APIs can be protected against injection attacks with a positive security model, and how 42Crunch easily enables such a model. Now, it’s time for the Spring4Shell (CVE-2022-22965) vulnerability, targeting the Spring framework, commonly used to build APIs. What can […]

Why Developer-First API Security is Prevailing in Enterprise
Why Developer-First API Security is Prevailing in Enterprise. The DevSecOps movement has led to a distinct “shift-left” in the enterprise where tasks are moved earlier in the development cycle so that developers can directly address production concerns as the code is being written. Companies are realizing greater business benefits from this shift-left approach, with accelerated […]
How Developers Can Become API Security Champions
Question: Everyone is talking about DevSecOps, why are we not able to fix the security issues? Despite the obvious challenges, Colin believes that the industry has made progress as compared to ten years ago when very insecure code was prevalent. Today’s code is definitely more secure and security is improving — thankfully most developers are […]
Why Do APIs Merit a Separate OWASP Top 10 Listing?
Throughout the 3 part webinar series “API Security Landscape Today and the OWASP API Security Top 10 Challenges” we will publish blog posts that highlight some of the main talking points addressed by the speakers. In this post, Philippe and Colin explore the differences between APIs and web apps that necessitated the creation of a […]

Protecting your APIs against Log4Shell with 42Crunch
On December 9th, 2021, the log4shell vulnerability hit the news and it has since been every security team’s worst nightmare: trivially exploitable, huge impact with RCE (Remote Code Execution), on a component widely used across traditional enterprise technological stacks, both in in-house and third-party software. All this combined explains its CVSS rating of 10 – […]

7 Ways to Avoid JWT Security Pitfalls
Dec 22nd 2021. Author: Dr. Philippe de Ryck, Pragmatic Web Security, Like them or hate them, JSON Web Tokens (JWT) are everywhere. OAuth 2.0 and OpenID Connect rely heavily on JWTs. Many applications use JWTs to implement custom security mechanisms. And every language or framework offers plenty of support for JWTs. Unfortunately, JWTs also lie […]

Application Security Tools Are Not up to the Job of API Security
The last two decades have seen a proliferation of software (according to GitHub there has been a 35% increase in code repositories in 2020 alone) into every aspect of our lives in the form of web or mobile applications. Adversaries have increasingly attacked these applications, and defenders have adopted various testing tools and technologies to […]
How to test API security throughout the API lifecycle with Postman and 42Crunch
Postman, the API collaboration platform for developers, advocates an API-First approach for companies. Using 42Crunch, API developers and application security teams can now implement API security design and testing as part of their API-First approach in Postman. Kin Lane, chief Evangelist with Postman recently joined Isabelle Mauny, Field CTO at 42Crunch for a webinar to […]

Creating High Quality OAS Definitions with .Net Core
This document highlights how code annotations can be used to enhance the quality and the security posture for customers using .Net Core. 42Crunch security recommendations help enterprises discover and remediate vulnerabilities much more quickly (up to 25X more quickly) while saving 90% of manual costs (whether through internal efforts or external pen-testing). Using the Available […]

Creating High Quality OAS Definitions with Springfox – Part 2: Data Validation
In the first part of this blog, we had covered the security aspects of Spring Boot Microservices and how to inject them into your code level to generate higher quality OAS (Swagger) files. In this second part, we will cover aspects regarding attributes, operations, and data. Data Validation for Secure APIs You must be aware […]

Strengthening Your API Security Posture – Ford Motor Company
LOSING MY RELIGION: Successful and unsuccessful approaches to API Security in a global enterprise – A take on Ford Motor Company’s approach to API security and the journey to enforce security compliance while ensuring productivity of thousands of developers managing thousands of APIs. The Cybersecurity Snowball Effect With development Communities and product teams, there are […]

Creating High Quality OAS Definitions with Springfox – Part 1: Security Definitions
Spring Boot is a popular framework to build applications and APIs. Leveraging the Springfox project and code annotations, developers can generate OAS files with a high 42Crunch Security Audit score. What is the 42Crunch Security Audit? The 42Crunch Security Audit is one of 3 services from the 42Crunch API Security Platform: it consumes OpenAPI (Swagger) […]

Questions Answered: How to Best Leverage JWTs or API Security
You had questions, and we’ve got answers! Thank you for all the questions submitted on our webinar: “How to Best Leverage JWTs or API Security” We were unable to get to your questions, so below are all the answers to the questions that were asked! If you’d like more information please feel free to contact […]

Why knowing is better than guessing for API Threat Protection
Why do we need different solutions for API Threat protection? APIs are becoming a hot target for hackers. Analysts and cyber security specialists agree that the privileged position of APIs as the open doors to the enterprise kingdom make them a favorite to breach. For the past 20 years, Web Application Firewalls (WAFs ) have […]

Questions Answered: OpenAPI for API Security
You had questions, and we’ve got answers! Thank you for all the questions submitted on our webinar: “OpenAPI for API Security – Why guess when you know?!” Below is the replay and all the answers to the questions that were asked. If you’d like more information please feel free to contact us. Webinar: OpenAPI for […]

Questions Answered: Let’s shift API security left – sure, but how?
You had questions, and we’ve got answers! Thank you for all the questions submitted on our webinar: “Let’s shift API security left – sure, but how?” Below is the replay and all the answers to the questions that were asked. If you’d like more information please feel free to contact us. [xyz-ihs snippet=”Webinar-Lets-Shift-API-Security-Left”] Don’t […]

42Crunch approach vs. Traditional WAF approach: using positive security by default
When talking to prospects or presenting our solution at conferences, we inevitably get asked the same question: what’s the difference between your solution and a Web Application Firewall (WAF)? The core difference is that we know what we are protecting, WAFs don’t. WAFs were built to protect web applications and there is no standard way […]

Questions Answered: 42Crunch Security Audit for WSO2 API Manager 3.1
You had questions, and we’ve got answers! Thank you for all the questions submitted on our “42Crunch Security Audit for WSO2 API Manager 3.1” webinar. Below is the replay and all the answers to the questions that were asked. If you’d like more information please feel free to contact us. [xyz-ihs snippet=”WSO2-Webinar”] […]

Questions Answered: Top API Security Issues Found During POCs
You had questions, and we’ve got answers! Thank you for all the questions submitted on our “Top API Security Issues Found During POCs” webinar. Below is the replay and all the answers to the questions that were asked. If you’d like more information please feel free to contact us. Is there a way to add […]

Questions Answered: The Anatomy of Four API Breaches
You had questions, and we’ve got answers! Thank you for all the questions submitted on our “The Anatomy of Four API Breaches” webinar. Below is the replay and all the answers to the questions that were asked. If you’d like more information please feel free to contact us. [xyz-ihs snippet=”Anatomy-API-Breach”] Does the implementation […]

Questions Answered: REST API Security by Design with Azure Pipelines
You had questions, and we’ve got answers! Thank you for all the questions submitted on our “REST API Security by Design with Azure Pipelines” webinar. Below are all the answers to the questions that were asked. If you’d like more information please feel free to contact us. REST API Security for Microsoft Azure Pipelines. Watch Webinar REST […]

Questions Answered: Protecting Microservices APIs with 42Crunch API Firewall
You had questions, and we’ve got answers! Thank you for all the questions submitted on our “Protecting Microservices APIs with 42Crunch API Firewall” webinar. Below are all the answers to the questions that were asked. If you’d like more information please feel free to contact us. [xyz-ihs snippet=”Protecting-microservices”] Can the sidecar be […]

Questions Answered: Are you properly using JWTs?
You had questions, and we’ve got answers! Thank you for all the questions submitted on our “Are you properly using JWTs?” webinar. Below are all the answers to the questions that were asked. If you’d like more information please feel free to contact us. [xyz-ihs snippet=”Jwt-webinar”] Is it considered safe if the […]

42Crunch API Firewall and API Management: why you need both!
Every day, new breaches show us that we still have a long way to go with API security. In order to protect APIs, enterprises need to take a holistic approach, which includes the following: Securing the infrastructure: OS configuration, network configuration as well as containers. Properly configuring application servers: enforce TLS 1.2/1.3, remove weak cipher […]

Questions Answered: Positive Security for APIs Webinar
You had questions, and we’ve got answers! Thank you for all the questions submitted on the Positive Security for APIs: What it is and why you need it! We couldn’t get to all of them so we wanted to follow-up with a full list of all the Q&A – and the slide deck as well! [xyz-ihs […]

OWASP API Security Top 10 Cheat Sheet
Download our OWASP API Security Cheat Sheets to print out and hang on your wall! Download Cheat Sheet If you missed our latest presentation, check out the slides here: Learn more about the OWASP API Security Top 10. Try our security audit for free. If you want to see the whole platform in action, […]

Questions Answered: OWASP API Security Top 10 Webinar
You had questions, and we’ve got answers! Thank you for all the questions submitted on the OWASP API Security Top 10 webinar on Nov 2019. We couldn’t get to all of them so we wanted to follow-up with a full list of all the Q&A – and the slide deck as well! How do you […]

Deploying DevSecOps for APIs: a tale of shifting left…
DevSecOps is a hot topic at the moment, and particularly relevant when dealing with API development. APIs are growing at an exponential rate: not only are they the backbone of any application, but microservices architecture imply exposing internal APIs for every microservice or group of microservices. The average number of APIs to protect within an […]

Addressing Harbor Registry Vulnerability with 42Crunch
Hot from the press! There is a mass assignment vulnerability in the Harbor registry. Mass assignment is entry A6 on the OWASP API Security Top 10 list. A6 is described in the OWASP API Security Top 10 as: An API endpoint is vulnerable if it automatically converts client parameters into internal object properties without considering […]

API Security is not Web Application Security!
When we started 42Crunch 3 years ago, we were convinced that a new market segment would emerge: API security. And the market is now catching up with our vision! This is exemplified by the recent release of the OWASP Top 10 for API Security threats document, which highlights threats that do not apply to traditional […]

We Need the Controller Layer Back!
A couple days ago, I gave an API security workshop to highlight the OWASP Top 10 issues for APIs and some of the mistakes we keep doing at development time and pay for at runtime. Many of the issues related to data, such as improper data filtering, mass assignment or excessive data exposure, could be […]

Revolutionizing API Security – 42Crunch + Digital Anarchist
42Crunch CEO, Jacques Declas, sat down with Alan Shimel of Digital Anarchist at this year’s RSA APJ show to discuss new trends in API Security, DevSecOps, and what tools you need to keep up! [Alan Shimel] Hey everyone, it’s Alan Shimel for DevOps.com Security Boulevard. We’re here in Singapore at RSA APJ. We’re right […]
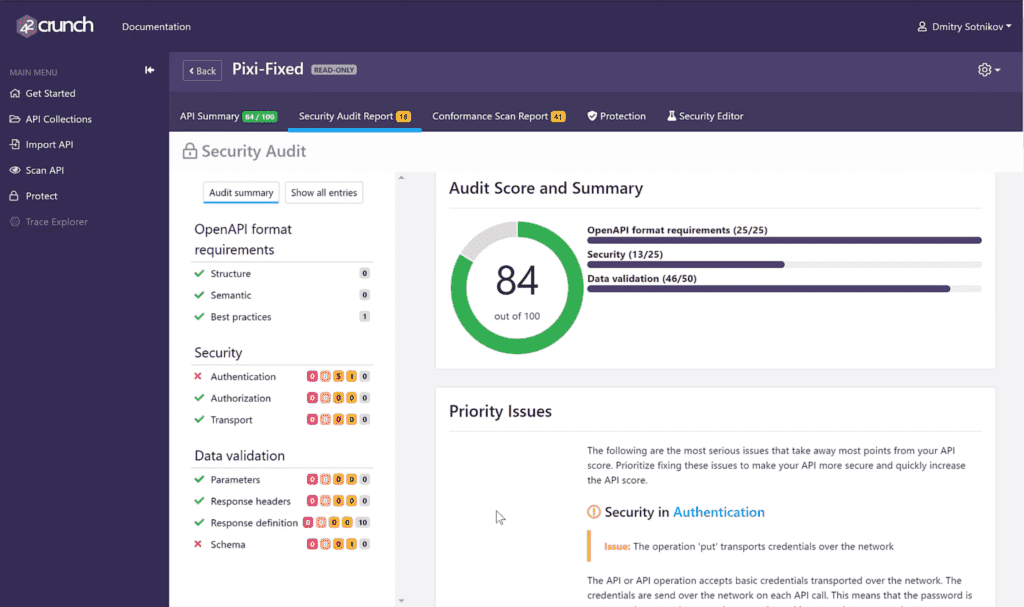
Enhance Your DevSecOps Experience with the 42Crunch API Security Platform
The 42Crunch platform offers DevSecOps teams a unique set of integrated API security tools which allow discovery, remediation of OpenAPI vulnerabilities and runtime protection against API attacks. The 42Crunch June 2019 release introduces an updated, easy to use UI along with key enhancements to API contract security audit reports, full user management for organization administrators, […]

Hot off the press: the OWASP API Security Top 10 list!
Last week, a new OWASP project was launched at the Global AppSec conference in Tel Aviv: the API Security Top 10 list. The project information and initial Top 10 list were presented by Erez Yalon (Checkmarx) and Inon Shkedy and you can download the presentation PDF. We have also created an OWASP API Security Top […]

API Security: separating truth from fiction
Where is the truth and what’s the fiction ? In this webinar Alexei Balaganski, Lead Analyst at Kuppinger Cole and myself contrasted our experience with customers and prospects and came up with a list of facts and fictions about API security. We both have seen a surge of interest in API security after a challenging […]

Token Management Security Best Practices
We recently participated to the DZone mobile apps development guide to highlights some of the key best practices when dealing with API keys and tokens. Below is an excerpt, the full article is available on DZone! Modern applications, both web-based and native, rely on APIs on the backend to access protected resources. To authorise access […]

API Security FAQ : the top 5 questions we answered at the APIWorld conference!
The APIWorld conference came to end last week. This was the first public preview of our platform! We had a blast talking to many attendees and presenting at the event. This also gave us the opportunity to address a few common questions relative to API security and our product. 1. I have seen 3 vendors […]

Start acting on API Security today!
APIs are the access doors to your enterprise assets and the backbone of pretty much any application that has been written in recent years. While most companies apply token-based access to APIs with OpenIDConnect and OAuth, there are still many aspects of security which are not properly covered for APIs such as common injection attacks, […]

Why do we need the A10 entry in the OWASP Top 10?
Without any doubt, APIs have redefined the enterprise architecture landscape by becoming the building blocks of internal and external enterprise applications. APIs are now the entry point into most architectures, much like servlets and JSPs were in the application server era. APIs give access to a wide range of applications, systems, databases and now things with […]
Secure Your APIs Today
#1 API security platform



