Resources
A full list of Blogs, Webinars, Press Releases, News ...
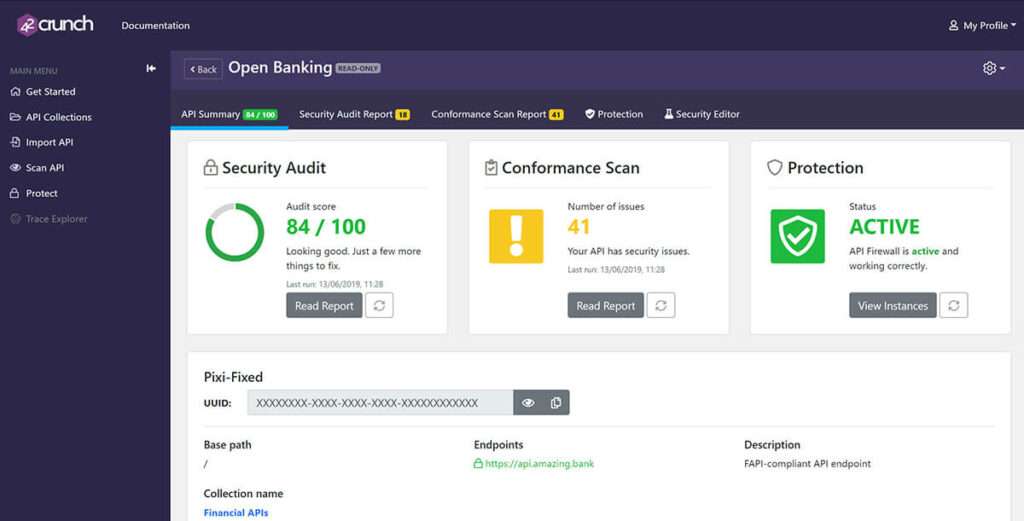
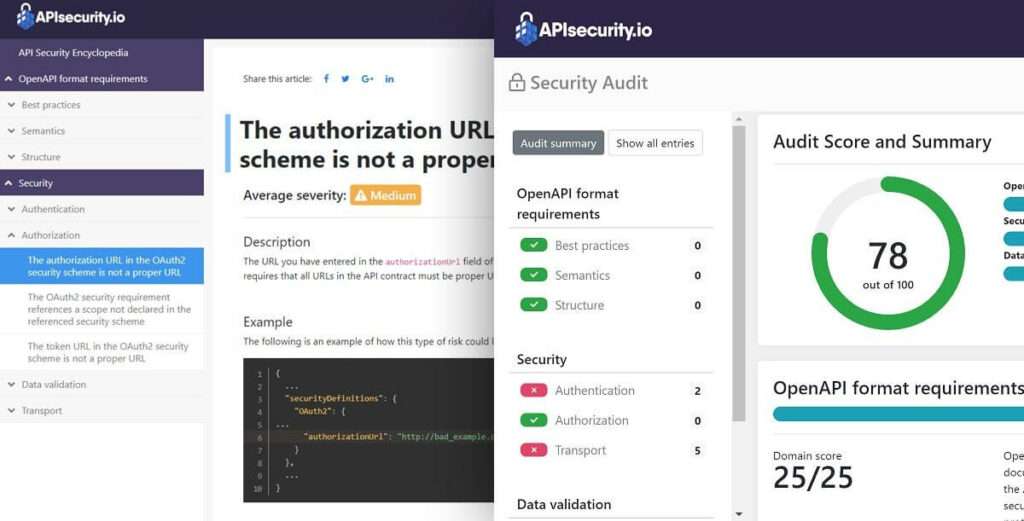
OpenAPI (Swagger) Security Audit Report Explained
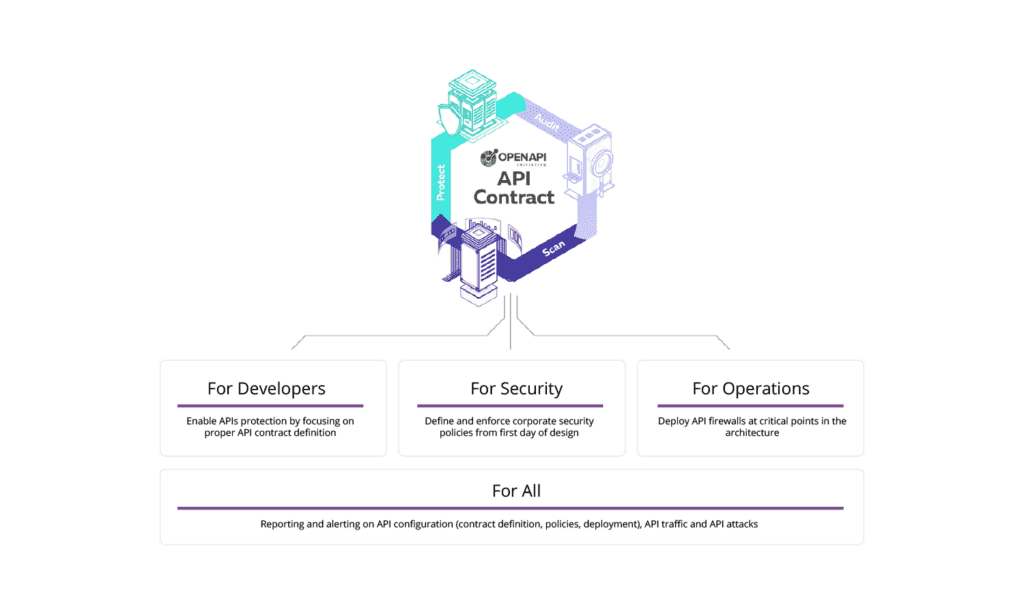
Tutorials In our previous tutorial, we have created an API collection, and imported and audited an OpenAPI (Swagger) definition file. Now we are going to drill into the report and walk you through how to get the most out of it. Viewing Checks API Contract Security Audit is a static analysis of your OpenAPI (Swagger) file using OpenAPI Specification. We run 300+ checks on your API definition, and you can...
Questions Answered: 42Crunch Security Audit for WSO2 API Manager 3.1
You had questions, and we've got answers! Thank you for all the questions submitted on our "42Crunch Security Audit for WSO2 API Manager 3.1" webinar. Below is the replay and all the answers to the questions that were asked. If you'd like more information please feel free to contact us. [xyz-ihs snippet="WSO2-Webinar"] Is this audit feature available with the community version of WSO2? Yes it is....
Fixing API Security Issues identified in the Audit Report
Tutorials In our previous tutorial, we took a look at the audit report from API Contract Security Audit. This one proceeds onto fixing the issues found in the audit and see how we can iteratively work on our OpenAPI / Swagger definition. Navigating Issues The best place to start are the high priority issues, they are the fastest way to improve the audit score. For example, in the audit report,...
API Security Testing with API Scan
Tutorials We are going to show you how to perform a conformance scan on our platform. You can also perform an API Scan in VS code IDE (platform registration is required). You can register for free. API Scan is a dynamic runtime testing tool that simulates real traffic to your API to ensure conformance with the OpenAPI contract and identify security vulnerabilities. Dynamic Testing API Contract Conformance Scan is a...
API Protect Micro API Firewall
Tutorials In previous tutorials, we have covered static analysis with the API security audit, dynamic testing with conformance scan - now it's time to discuss protection. The Protection function is real-time protection of live APIs. Protection Overview You put our API firewall in the line of traffic. It's an extremely efficient piece of software that we ship as a docker image. It's been written in C, is highly optimized, less...
API Protect Micro API Firewall Reports and Troubleshooting
Tutorials You've seen how 42Crunch can protect your APIs and microservices - now let's review reporting. Viewing Transaction Logs At any time, you can click on transaction logs to view all failed transactions found by the conformance scan and review the full list. Look up a Specific Error So one thing that I want to show first is how you can troubleshoot and see that specific transactions that get blocked....
42Crunch Security Audit for WSO2 API Manager 3.1
Webinar WSO2 API Manager 3.1 brings a lot of interesting features including the ability to run 42Crunch's audit tool directly from the API Publishing portal. In this webinar, we will: Explain the advantages of introducing security at design time Introduce the 42Crunch audit functionality Explain how 42Crunch and WSO2 API Manager can be used together for better API Security Demo the integration Special Guest Presenters: Sanjeewa Malalgoda, Associate Director -...
Questions Answered: Top API Security Issues Found During POCs
You had questions, and we've got answers! Thank you for all the questions submitted on our "Top API Security Issues Found During POCs" webinar. Below is the replay and all the answers to the questions that were asked. If you'd like more information please feel free to contact us. Is there a way to add specific rules to the allowlist? There are two things you can do today: one is...
Top API Security Issues Found During POCs
Webinar Over the past 6 months, we have discovered many similarities across APIs from companies from very different industries. "This is an eye opener" is the most recurring comment from our prospects. We thought it would be worth sharing our findings in this webinar. Through a mix of slides and demos, we will describe the top 5 issues our security audit reports, what they are and why they matter, including:...
Questions Answered: The Anatomy of Four API Breaches
You had questions, and we've got answers! Thank you for all the questions submitted on our "The Anatomy of Four API Breaches" webinar. Below is the replay and all the answers to the questions that were asked. If you'd like more information please feel free to contact us. [xyz-ihs snippet="Anatomy-API-Breach"] Does the implementation of OAuth2 mitigate the risks you mentioned? OAuth2 is one of the tools you need...
OpenAPI Swagger Editor Extension in VS Code
Tutorials The 42Crunch OpenAPI Editor extension in VS Code explained Introducing the OpenAPI Editor Why using the OpenAPI editor will save you time and effort creating and editing OpenAPI files. How to install the OpenAPI Editor A quick run through on the installation of the 42Crunch OpenAPI Editor in VS Code. List of the OpenAPI Editor extensions in IDEs Navigating with the OpenAPI Explorer Learn how to quickly navigate through...
API Security Audit using OpenAPI Swagger Editor Extension in VS Code
Tutorials Identify and fix issues in the OpenAPI (formerly Swagger) definition file using the API Audit, available via the OpenAPI Editor in Microsoft Visual Studio Code (VS Code). Reviewing The Score API audit runs over 300 different checks and provides an overall score that represents the quality of your OpenAPI definition. Learn more by viewing the explanatory video. Filtering The Audit Report There are a number of ways to filter...
The Anatomy of API Breaches
Webinar Watch the Webinar Browse the Deck Securing APIs implies securing the infrastructure but also the APIs themselves. Unfortunately, having all possible infrastructure protections in place is only one aspect of the recent OWASP Top10 for API Security. Other issues such as data leakage, mass assignment or broken authentication/authorization must be handled at the application level. In the past year or so, more than 200 breaches have been published on...
Questions Answered: REST API Security by Design with Azure Pipelines
You had questions, and we've got answers! Thank you for all the questions submitted on our "REST API Security by Design with Azure Pipelines" webinar. Below are all the answers to the questions that were asked. If you'd like more information please feel free to contact us. REST API Security for Microsoft Azure Pipelines. Watch Webinar REST API Security for Microsoft Azure Pipelines Slide Deck Download I know this API Security Audit requires a...
REST API Security for Microsoft Azure Pipelines
Webinars Watch the Webinar Browse the Deck Security is an important topic in software development. Unfortunately, security is usually considered too late in software development, and especially in the API lifecycle. Waiting until software and APIs are in production before addressing security concerns can be a severe risk to your organization. Did you know that vulnerabilities found in production cost up to 30x time and money more to fix? There...
42Crunch Launches New REST API Static Security Testing Extension for Azure Pipelines
Enables Azure DevOps customers to extend their DevSecOps practices to REST APIs IRVINE, CA, MARCH 18, 2020 — Today, the API security leader and creator of REST API DevSecOps tooling and the industry’s first API Firewall, 42Crunch, announced the launch of their new REST API Static Security Testing extension for Microsoft Azure Pipelines. This extension enables companies to easily enforce secure API design right from their CI/CD pipeline. With REST...
42Crunch Adds Self Registration and Low-cost Tiers to API Security Platform
42Crunch Democratizes API Security by Adding Self Registration, Free and Low-Cost Tiers to Their Comprehensive API Security Platform SAN FRANCISCO, FEBRUARY 25, 2020 — Today at the RSA Conference, API security leader and creator of the industry’s first API Firewall – 42Crunch – announced the launch of its new self-registration feature for their API Security Platform. Development, security and operations teams now have instant access to a comprehensive set...
Questions Answered: Protecting Microservices APIs with 42Crunch API Firewall
You had questions, and we've got answers! Thank you for all the questions submitted on our "Protecting Microservices APIs with 42Crunch API Firewall" webinar. Below are all the answers to the questions that were asked. If you'd like more information please feel free to contact us. [xyz-ihs snippet="Protecting-microservices"] Can the sidecar be tested somehow? Yes, the configuration is tested before it is made available to the API...
Questions Answered: Are you properly using JWTs?
You had questions, and we've got answers! Thank you for all the questions submitted on our "Are you properly using JWTs?" webinar. Below are all the answers to the questions that were asked. If you'd like more information please feel free to contact us. [xyz-ihs snippet="Jwt-webinar"] Is it considered safe if the JWT token is validated within the Asp.Net Core itself with every request. Like when it’s...
Protecting Microservices APIs with 42Crunch API Firewall
Webinar In loosely coupled architectures, we must put in place application level security, should it be for client traffic (North-South) or intra-microservices traffic (East-West). In this webinar, we show you how the 42Crunch API firewall can be used to put API threat protection in place automatically, as early as design time. We'll use a mix of slides and demos to present: The various elements of security to consider in order...
Are You Properly Using JWTs?
Webinar JSON Web tokens (JWTs) are used massively in API-based applications as access tokens or to transport information across services. Unfortunately, JWT are often mis-used and incorrectly handled. Massive data breaches have occurred in the last 18 months due to token leakage and lack of proper of validation. This session focuses on best practices and real-world examples of JWT usage, where we cover: Typical scenarios where using JWT is a...
42Crunch API Firewall and API Management: why you need both!
Every day, new breaches show us that we still have a long way to go with API security. In order to protect APIs, enterprises need to take a holistic approach, which includes the following: Securing the infrastructure: OS configuration, network configuration as well as containers. Properly configuring application servers: enforce TLS 1.2/1.3, remove weak cipher suites, eventually enforce mutual SSL, use security headers, use secure cookies, use latest versions of...
42crunch and Yenlo Announce Partnership
Amsterdam and Paris, December 18, 2019 – Global integration- and API management specialist Yenlo and specialist in API security 42Crunch, today announced a strategic partnership to secure and enforce API-policies as an added value service to Yenlo’s growing API business across the world. 42Crunch offers an enterprise-grade, full-fledged, end-to-end API security platform. Using the 42Crunch platform, enterprises have a unique set of integrated API security tools that allow discovery, remediation of OpenAPI vulnerabilities,...
Questions Answered: Positive Security for APIs Webinar
You had questions, and we've got answers! Thank you for all the questions submitted on the Positive Security for APIs: What it is and why you need it! We couldn't get to all of them so we wanted to follow-up with a full list of all the Q&A - and the slide deck as well! [xyz-ihs snippet="Positive-Security"] How does the tool work, does it do a code scan across...
OWASP API Security Top 10 Cheat Sheet
Download our OWASP API Security Cheat Sheets to print out and hang on your wall! Download Cheat Sheet If you missed our latest presentation, check out the slides here: Learn more about the OWASP API Security Top 10. Try our security audit for free. If you want to see the whole platform in action, request a demo now!
Positive API Security Model, and Why You Need It!
Webinar Many of the issues on the OWASP API Security Top 10 are triggered by the lack of input or output validation. To protect APIs from such issues, an API-native, positive security approach is required: we create an allowlist of the characteristics of allowed requests. These characteristics are used to validate input and output data for things like data type, min or max length, permitted characters, or valid values ranges....
Questions Answered: OWASP API Security Top 10 Webinar
You had questions, and we've got answers! Thank you for all the questions submitted on the OWASP API Security Top 10 webinar on Nov 2019. We couldn't get to all of them so we wanted to follow-up with a full list of all the Q&A - and the slide deck as well! How do you find all the API endpoints in web applications? A few ways that you can do...
OWASP API Security Top 10
Webinar November 21, 2019 Watch the Webinar Browse the Deck In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches - APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns...
Deploying DevSecOps for APIs: a tale of shifting left…
DevSecOps is a hot topic at the moment, and particularly relevant when dealing with API development. APIs are growing at an exponential rate: not only are they the backbone of any application, but microservices architecture imply exposing internal APIs for every microservice or group of microservices. The average number of APIs to protect within an enterprise is nearing 500. In that context, how do we : Ensure consistency across all...
42Crunch Adds API Security Audit to its Visual Studio Code OpenAPI Extension
SAN JOSE, OCTOBER 9, 2019 — Today at API World, API security leader and creator of the industry’s first API Firewall, 42Crunch, announced the availability of REST API Security Audit functionality in its popular OpenAPI extension for Microsoft Visual Studio Code — making it easier than ever to enable a DevSecOps process for API security. Developers working on their APIs within 42Crunch’s VS Code extension simply have to click the...
Addressing Harbor Registry Vulnerability with 42Crunch
Hot from the press! There is a mass assignment vulnerability in the Harbor registry. Mass assignment is entry A6 on the OWASP API Security Top 10 list. A6 is described in the OWASP API Security Top 10 as: An API endpoint is vulnerable if it automatically converts client parameters into internal object properties without considering the sensitivity and the exposure level of these properties. This could allow an attacker to...
API Security is not Web Application Security!
When we started 42Crunch 3 years ago, we were convinced that a new market segment would emerge: API security. And the market is now catching up with our vision! This is exemplified by the recent release of the OWASP Top 10 for API Security threats document, which highlights threats that do not apply to traditional web applications. In other words, if your security products protect you against the traditional OWASP...
We Need the Controller Layer Back!
A couple days ago, I gave an API security workshop to highlight the OWASP Top 10 issues for APIs and some of the mistakes we keep doing at development time and pay for at runtime. Many of the issues related to data, such as improper data filtering, mass assignment or excessive data exposure, could be avoided if data was controlled in a specific layer of the architecture. When I started...
New API Firewall Non-blocking Mode in Latest 42Crunch Release
The 42Crunch August 2019 release introduces a new API firewall non-blocking mode so you can test how it affects your existing API traffic without impacting consumers, a deeper integration between the security audit and editor for seamless navigation, and an enhanced audit issue view for faster editing. (See the release notes for additional details on full list of updates.) New Feature Highlights API Firewall Non-blocking Mode 42Crunch leverages the API contract...
Revolutionizing API Security – 42Crunch + Digital Anarchist
42Crunch CEO, Jacques Declas, sat down with Alan Shimel of Digital Anarchist at this year's RSA APJ show to discuss new trends in API Security, DevSecOps, and what tools you need to keep up! [Alan Shimel] Hey everyone, it’s Alan Shimel for DevOps.com Security Boulevard. We’re here in Singapore at RSA APJ. We’re right on the edge of the show floor interviewing speakers, attendees, vendors – just getting the...
42Crunch Adds OpenAPI Editing Tools to its API Security Platform
Enables Any Developer to Become a Security Expert and the Driving Force Of API Security IRVINE, AUGUST 6, 2019 — Today, API security leader and creator of the industry’s first API Firewall, 42Crunch, announced the latest release of its API security platform with enhanced tools for developers to easily define security in OpenAPI contracts — enabling an agile DevSecOps experience, and providing full visibility into each individual API’s security landscape. ...
42Crunch Announces Full Kubernetes Support to Automate Zero-Trust API Security Across Microservices Architecture
42Crunch Allows Organizations to Extend Comprehensive API Security Beyond the Edge, to Each and Every Container in Kubernetes Environments SINGAPORE, JULY 16, 2019 — Today at RSA Asia Pacific & Japan 2019, API security leader and creator of the industry’s first API Firewall – 42Crunch – announced the latest release of its API security platform with full support for Kubernetes environments. This new solution allows organizations to easily automate API...
Enhance Your DevSecOps Experience with the 42Crunch API Security Platform
The 42Crunch platform offers DevSecOps teams a unique set of integrated API security tools which allow discovery, remediation of OpenAPI vulnerabilities and runtime protection against API attacks. The 42Crunch June 2019 release introduces an updated, easy to use UI along with key enhancements to API contract security audit reports, full user management for organization administrators, support for DevSecOps using our REST API, and built-in user interface to look up API...
Hot off the press: the OWASP API Security Top 10 list!
Last week, a new OWASP project was launched at the Global AppSec conference in Tel Aviv: the API Security Top 10 list. The project information and initial Top 10 list were presented by Erez Yalon (Checkmarx) and Inon Shkedy and you can download the presentation PDF. We have also created an OWASP API Security Top 10 Cheat Sheet that you may download. The initial list is: A1: Broken Object Level...
Leading API Security Platform, 42Crunch, Launches Partner Network
MUNICH, GERMANY. MAY 14, 2019 -- Today at the European Identity & Cloud Conference (EIC) 2019, API security leader and creator of the industry’s first API Firewall - 42Crunch - announced the launch of its reseller and implementation partner program, as well as the first two commercial partnerships with Skalena (Brazil) and atSistemas (Spain). The launching of a regional network of resellers and implementation partners will be able to resell...
API Security: separating truth from fiction
Where is the truth and what's the fiction ? In this webinar Alexei Balaganski, Lead Analyst at Kuppinger Cole and myself contrasted our experience with customers and prospects and came up with a list of facts and fictions about API security. We both have seen a surge of interest in API security after a challenging 2018: breaches through APIs are accelerating at a high pace and it's only the beginning....
42Crunch announces the launch of the first API Security platform
IRVINE, CA, USA, March 6, 2019 -- 42Crunch, the leading API security company, announced today the release of the 42Crunch API Platform, the world’s first API security cloud platform to discover vulnerabilities in APIs and protect them from attack. The 42Crunch Platform can protect SaaS, Web, or IoT APIs, as well as microservices. This follows the launch of the free API Contract Security Audit tool at APISecurity.io earlier this month. The tool helps API developers...
APIsecurity.io adds API Security issues and a free API Contract Security Audit service
LONDON, UK, February 13, 2019 -- API Contract Security Audit is a free online tool that lets developers and security professionals upload their OpenAPI definition files and get a detailed security assessment on the potential risks that their APIs might have. Each issue in the report shows the specific place in the API contract that may cause trouble, provides details on the potential exploit scenario, and shows recommendations on how...
42crunch and CriticalBlue announce partnership
London – Nov 21, 2018 – Today, at the API Security For Open Banking Summit, 42Crunch, the leading backend API security platform and CriticalBlue, provider of Approov, the leading frontend mobile API security solution, announced that they are now offering enterprise customers with an end-to-end API protection service. 42Crunch and CriticalBlue were both named Cool Vendors by Gartner in 2017. Misuse and abuse of APIs is a real and growing threat....
Token Management Security Best Practices
We recently participated to the DZone mobile apps development guide to highlights some of the key best practices when dealing with API keys and tokens. Below is an excerpt, the full article is available on DZone! Modern applications, both web-based and native, rely on APIs on the backend to access protected resources. To authorise access those APIs, a request must include some kind of access token or key. This article...
42Crunch launches APISecurity.io, hires Dmitry Sotnikov as the VP of Cloud Platform
IRVINE, CA, USA, November 5, 2018 -- 42Crunch announced today that it has launched APISecurity.io, an online API Security hub that includes, for example, a weekly newsletter, industry news, information on recent breaches and vulnerabilities, standards, regulations, and tools. APISecurity.io provides API developers the much needed single source for up-to-date and relevant information around API Security which has not really been available until now. The APISecurity.io effort is one of...
42Crunch partners with Kudelski IoT Security group
CHESEAUX-SUR-LAUSANNE, Switzerland and PHOENIX (AZ), USA, December 20, 2017 – The Kudelski Group (SIX:KUD.S), the world leader in digital security, will demonstrate its IoT Security Suite at CES® 2018. The comprehensive suite of services and technologies targets device manufacturers and service providers who need solid security foundations in order to enable long-term monetization, privacy and safety of their devices and enable new sustainable business models. The suite and several applications...
API Security FAQ : the top 5 questions we answered at the APIWorld conference!
The APIWorld conference came to end last week. This was the first public preview of our platform! We had a blast talking to many attendees and presenting at the event. This also gave us the opportunity to address a few common questions relative to API security and our product. 1. I have seen 3 vendors on the conference floor, they all define API Security differently! Glad you asked:) API security...
Start acting on API Security today!
APIs are the access doors to your enterprise assets and the backbone of pretty much any application that has been written in recent years. While most companies apply token-based access to APIs with OpenIDConnect and OAuth, there are still many aspects of security which are not properly covered for APIs such as common injection attacks, keys and certificates secured storage, fine-grain access to resources, non-repudiation, or simply message encryption. Also,...
Why do we need the A10 entry in the OWASP Top 10?
Without any doubt, APIs have redefined the enterprise architecture landscape by becoming the building blocks of internal and external enterprise applications. APIs are now the entry point into most architectures, much like servlets and JSPs were in the application server era. APIs give access to a wide range of applications, systems, databases and now things with the expansion of IoT. In the latest edition of the Top 10 OWASP threats list,...
42crunch named a “Cool Vendor” in Monitoring and Management of Threats to Applications and Data
42Crunch today announced that it had been named a Cool Vendor by Gartner in its "Cool Vendors in Monitoring and Management of Threats to Applications and Data, 2017"[1] report, which was published on June 8, 2017. Gartner subscribers can access the report at https://www.gartner.com/doc/3742417?ref=SiteSearch&sthkw=cool%20vendor&fnl=search&srcId=1-3478922254 . The Gartner[2] report recommends that, "security and risk management leaders overseeing security monitoring and operations should utilize a security validation platform to determine if your...
Ready to Learn More?
Developer-first solution for delivering API security as code.